Home > Security IP > Root of Trust Solutions > RT-63x Programmable Root of Trust Family
The Rambus RT-63x Root of Trust IP are fully programmable FIPS 140-3 compliant hardware security cores with optional Quantum Safe security by design for data center, AI/ML, as well as general purpose semiconductor applications. They protect against a wide range of hardware and software attacks through state-of-the-art anti-tamper and security techniques.
As Edge AI and other applications requiring protection evolve, device and system architects face a growing array of security threats, including the threat from quantum computers. Across applications, one constant is the need for a hardware Root of Trust-based security implementation.
The RT-63x Root of Trust family employs a custom 32-bit RISC-V siloed and layered secure co-processor, along with dedicated secure memories. The RT-630 features several high-capability cryptographic accelerators such as AES, HMAC, SHA2/3, RSA, ECC, and a NIST-compliant Random Bit Generator. It is FIPS 140-2 CMVP Level 2 Certified. The RT-631 adds the OSCAA SM2/3/4 Chinese cryptographic accelerators. The RT-632 builds on the RT-630 adding ChaCha20 and Poly1305 cryptographic accelerators. The RT-634 takes the robust feature set of the RT-630 and offers a Quantum Safe Engine with CRYSTALS-Kyber and CRYSTALS-Dilithium, as well as XMSS and LMS stateful hash acceleration, to safeguard against quantum computer attacks.
Satisfying use cases such as identity management, (Caliptra) attestation, and secure boot, the RT-63x products are ideally suited for data center and AI/ML applications where FIPS 140-3 validation is required and security is a priority.
RT-600 Root of Trust Series A New Generation of Security Anchored in Hardware

This latest generation of the Rambus RT-600 Root of Trust IP offers many new features designed to support the security needs of customers today and into the future. These features include Quantum Safe Cryptography, Caliptra Root of Trust for Measurement (RoTM) emulation, an embedded physical unclonable function (PUF), as well as many architectural improvements, such as larger memory space and 64-bit addressing support.
How the Root of Trust Works
The Root of Trust is an independent hardware security co-processor design for integration into semiconductor devices, offering secure execution of user applications, tamper detection and protection, and secure storage and handling of keys and security assets. The Root of Trust offers chipmakers a siloed approach to security; while located on the same silicon as the main processor, the secure processing core is physically separated. A layered security approach enforces access to crypto modules, memory ranges, I/O pins, and other resources, and assures critical keys are available through hardware only with no access by software. The Rambus Root of Trust supports all common main processor architectures, including ARM, RISC-V, x86 and others.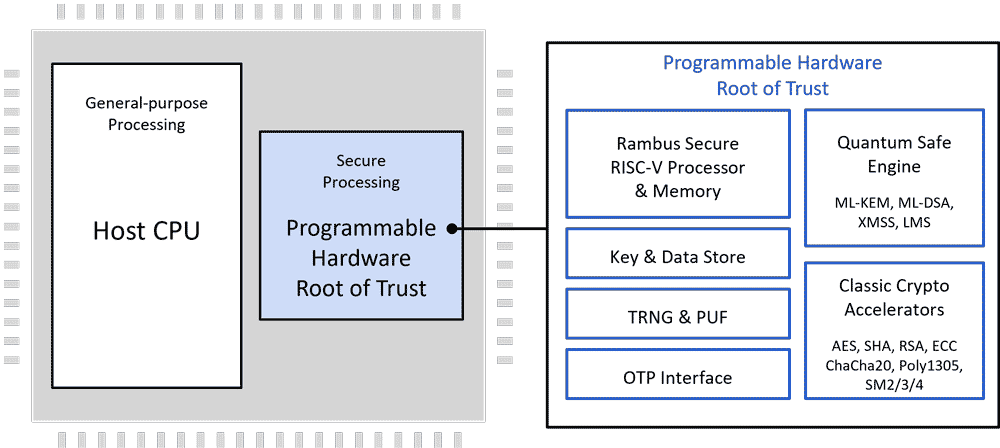
The Rambus Root of Trust supports multi-tenant deployments by offering true multiple root of trust capabilities. Each individual secure application can be assigned its own unique keys, meaning permissions and access levels are set completely independent of others. Secure applications are siloed from each other, ensuring the best approach to security. OEMs can determine access levels and permissions for each and all processes operating within the secure processor.
Dedicated FPGA configuration
The RT-630 is available in a FPGA configuration, targeting synthesis in programmable logic. This configuration is designed to map optimally (for max utilization and max frequency) into an FPGA fabric and connect either to on-board or external CPUs. In addition, the design is expanded with an additional OTP emulation model to overcome the lack of (or limitation of) true nonvolatile one-time programmable memory in certain FPGA families. This module allows storing secure assets in external flash in a secure way.
Secure Applications
Included with the RT-63x Hardware Root of Trust products are a series of standard secure applications (“containers”) to speed development, including secure boot, identity management, HSM reference, and others. A container development kit (CSDK) is also included to allow the development of custom containers for specific use cases.
Rambus can optionally offer dedicated FIPS 140-3 support packages to its licensees that provide FIPS 140-3 related certification documentation, FIPS test scripts, and dedicated FIPS support.
Protecting Data and Devices Now and in the Quantum Computing Era

Quantum computing is being pursued across industry, government and academia with tremendous energy and is set to become a reality in the not-so-distant future. Once sufficiently large quantum computers exist, traditional asymmetric cryptographic methods for key exchange and digital signatures will be broken. Many initiatives have been launched throughout the world to develop and deploy new quantum-resistant cryptographic algorithms, known as Post-Quantum Cryptography (PQC).
Solution Offerings
Superior Security
- Hardware Root of Trust
- Custom RISC-V security processor
- Multi-layered security model provides protection of all components in the core
- NIST CAVP and CMVP compliant for FIPS 140-3 validation
- NIST CAVP and CMVP certified for FIPS 140-2 validation
- Secure in-core processing and industry-leading anti-tamper
- OSCCA approved Chinese SM2, SM3, SM4 algorithm support
- Caliptra Root of Trust for Measurement with DICE and X.509 support
- TRNG and PUF entropy sources
- Quantum Safe Engine (QSE)
- Secure lifecycle management
- Secure provisioning with Rambus CryptoManager Root Server (CMRS)
Enhanced Flexibility
- 3rd-party applications run securely within trusted boundary, each with its own assigned security permissions
- Complete development environment allows OEMs and users to easily develop secure applications (”containers”); standard use case application containers provided
- Support for secure provisioning of keys and firmware at manufacturing or in the field
- Support for multiple Root of Trust instances within a single secure core
Security Models
- Hierarchical privilege
- Secure key management policy
- Hardware-enforced isolation/access control/protection
- Error management policy
Cryptographic Accelerators
RT-630: Includes AES (all modes), HMAC, SHA-2/3 (all modes), RSA up to 4096 or 8192 bits, ECC up to 521 bits, a NIST SP 800-90a/b/c Random Bit Generator, LMS and XMSS hash-based signature schemes, and SHAKE XOF
RT-631: As per RT-630 + Chinese Encryption with OSCAA SM2/3/4
RT-632: As per RT-630 + IoT Encryption with ChaCha20/Poly1305
RT-634: As per RT-630 + Quantum Safe Engine with CRYSTALS-Kyber and CRYSTALS-Dilithium
Security Modules
- Canary logic for protection against glitching and overclocking
- Secure key derivation and key transport
- Life cycle management
- Secure test and debug
- Feature management
Complete Documentation
- Integration guides
- Reference manuals
- Programming guides
RTL and FW Package
- Verilog RTL for synthesis and simulation
- Standard EDA tool flow scripts and support files
- Verification test bench and test vectors
- Boot loaders and secure RTOS and security monitor firmware
- HLOS APIs for accessing RT-63x capabilities
SW SDK Package
- SDK including the development environment, complete emulation with debugging capabilities of the RISC-V and crypto cores on QEMU
- One-step install emulation with multiple samples and reference code to help customers kickstart their secure application development
FIPS 140-3 Support Package (Optional)
- FIPS 140-3 test scripts
- FIPS 140-3 related certification documentation
- FIPS 140-3 support
Secure Applications
| Secure Application | Description |
|---|---|
| Linux Secure Boot | Implements secure boot for Linux OS, secured by the Root of Trust co-processor |
| Linux Secure FOTA | Implements secure Firmware Over the Air (FOTA) updates for Linux OS |
| Secure Boot | Uses the Root of Trust co-processor to assist in the secure boot process of ASICs and FPGAs |
| Secure Data Storage | Uses the Root of Trust co-processor to protect user credentials or biometric templates |
| Open SSL Hardening | Hardens the OpenSSL crypto operations via the Root of Trust secure co-processor |
| Reference HSM | Implements a basic HSM supporting AES, HMAC, SHA256, ECDSA, X.509 certificates and secure storage |
| Unique ID Generator | Creates a Root of Trust unique ID and stores it in the Root of Trust NVM (Non Volatile Memory) |




