
Are Tried and True Encryption Standards Going by the Wayside?
Michael Cobb, certified information systems security professional – information systems security architecture professional (CISSP – ISSAP), is regarded as a top security expert and is
Home > Provisioning & Key Management > Page 3

Michael Cobb, certified information systems security professional – information systems security architecture professional (CISSP – ISSAP), is regarded as a top security expert and is
EE Times India reports that the RISC-V instruction set architecture (ISA) has made significant progress in that country. It says that researchers at Indian Institute of
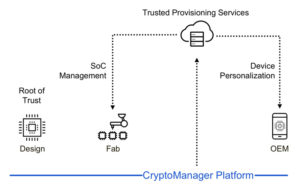
The latest news coming out of the security world is the link up of Micron’s Authenta™ secure memory product and Rambus’s CryptoManager™ infrastructure to add

Our world is growing increasingly connected, and while most people have reaped the benefits of interconnectivity, ranging from social networks to Internet of Things (IoT)

Dubbed “Foreshadow,” this speculative execution attack allows an attacker to steal sensitive information stored inside personal computers or third-party clouds. There are two versions: the original attack designed to extract data from Software Guard Extensions (SGX) enclaves and a next-generation version that affects virtual machines (VM), hypervisors, operating system kernel memory, and System Management Mode (SMM) memory. SGX is a new feature in modern CPUs which allows computers to protect users’ data, even if the entire system falls under the attacker’s control.

According to a new report published by Bain and Company, the combined markets of the Internet of Things (IoT) will grow to about $520 billion
