ICE-IP-63 High-Speed Inline Cipher Engine
Home > Security IP > Inline Memory Encryption IP > ICE-IP-63 High-Speed Inline Cipher Engine
The ICE-IP-63 (EIP-63) is a scalable high-performance, multi-channel cryptographic engine that offers AES-GCM operations as well as AES-CTR and GMAC on bulk data. Its flexible data path is suitable to scale from 100 Gbps to 2.4 Tbps to provide a tailored engine with minimal area for your application. The FIFO-like data interface makes it possible to perform frame processing for many different protocols, including MACsec, IPsec, and OTN security. The time-sliced processing architecture makes it possible to alternate data processing for different channels or tunnels simultaneously. Block switching can be done with a granularity of a single clock cycle. The engine is also designed to support FIPS vector processing.
The ICE-IP-63 is designed to support multiple use cases, including:
- Security for 5G Transport with FlexE
- TMS transport network: encryption for OTNsec and FlexO (ITU-T)
- PCIe or CXL (Compute Express) Link Encryption
- NVMe over Fabric Security
- Link Encryption: Security for any high-speed copper or fiber link with channel/link aggregation
- Applications where low and/or fixed latency operation is vital
How the ICE-IP-63 Multi-channel AES-GCM Engine Works
ICE-IP-63 is a packet-processing engine and contains input/output packet interfaces and interfaces intended for supplying key material.
Before cryptographic packet processing can start, the Host CPU must transfer the key material to the engine. The packet processing mode (bypass, encryption, authentication, direction, IV) is provided on a per packet basis.
After processing, the ICE-IP-63 engine outputs the result packet as well as ICV (if authentication is enabled).
The external system is responsible for the following items:
- Per-packet IV generation.
- Key lifetime management, ensures that the key is refreshed when the current key expires.
- Reacting on processing errors reported by the ICE-IP-63 engine
The ICE-IP-63 engine detects the following data path exceptions:
- IV counter overflow.
- When any RAM memory is read with an uncorrected error, its content cannot be trusted. Operation will continue normally but the report will be reported via an output pin.
- Uncorrectable ECC errors on data RAMs should be handled by an upper-layer module.
The ICE-IP-63 engine is ready for FIPS certification. This can be done by providing the FIPS CAVP validation vectors through the packet interface and performing the required transformations.
The following transformations are supported:
- AES-ECB encrypt (in CTR mode, using the IV as data input)
- AES-GCM encrypt/decrypt and authentication
- AES-CTR encrypt/decrypt
- AES-GMAC authentication
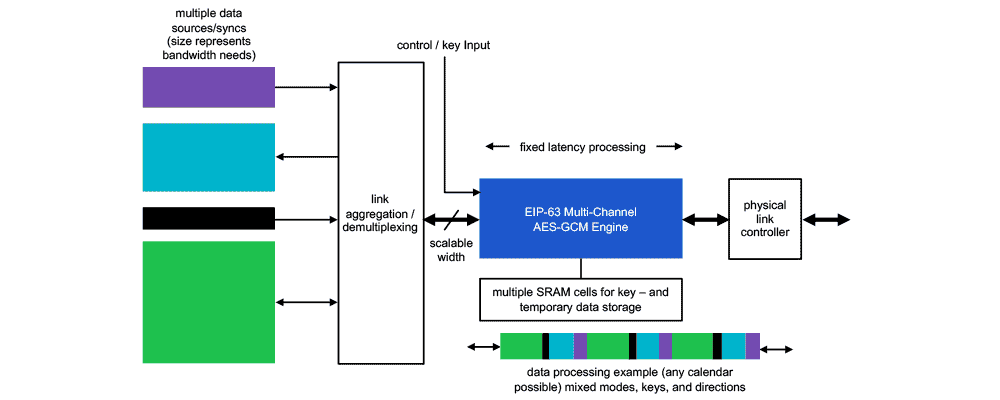
Configurations
The ICE-IP-63 engine has a scalable number of processing pipes and channels. It is available in different configurations, suitable for different applications to meet different gate count and throughput objectives. Available configurations scale from:- 1-12 parallel pipelines
- 128-1536 bits/clock
- >1600 MHz (16nm)
- Option for keys in registers or memories
- Configurations available from 400K gates
Verification
- Set of test vectors for chip integration verification
- Integration test vectors in a human-readable format
- Python / Verilog based verification environment
- 100% verification coverage
Full Disk Encryption of Solid State Drives and Root of Trust
File encryption, file system encryption and full disk encryption (FDE) are methods offered by the industry to allow users to protect their data stored on non-volatile storage devices, such as Solid State Disks (SSD). The main feature of FDE is to protect stored system and user date from unauthorized reading, writing, alteration, moving or rolling back. However, extended security features are key to securing FDE implementation.
Solution Offerings
Frame Processing Modes
- AES-GCM mode
- En/decryption-only mode: AES-CTR
- Authentication-only mode: AES-GMAC
- Any size packet bypassing
Cryptographic Processing
- Bi-directional design. Direction is selected on a per-packet basis
- Authenticated encryption, authenticated decryption: AES-GCM
- Authentication: AES-GMAC
- Encryption: AES-CTR
- Supported key sizes: 128 and 256 bits
- ICV output
- External 96-bit IV generation that allows supporting various use cases
Low Latency with Zero Variation
- Low-latency processing fixed to 20 clock cycles for AES-CTR only configurations and 24 clock cycles for AES-GCM and AES-CTR+GMAC configurations
Packet Interface
- Push-bus time-sliced interface (no handshake)
- Each data word may belong to a different channel
- Sideband signals for control and processing status
- Configurable bus width, depending on desired throughput in 128-bit units: minimum 128-bit, maximum 1536-bit
Control Plane Interface
- Key loading interface that can easily be mapped to a 32-bit wide host interface
- For each channel, 2 keys (current, next) can be loaded
External Memory interface
- Set of memory interfaces to buffer data and control information
- All interfaces are for 1R / 1W memory with 2 cycle read latency to allow inserting ECC logic
- ECC uncorrectable status input
- Some memories have per-word chip selection for efficient power usage
- Engine configurations with lower bus width and maximum number of channels requirements can be built with register storage instead
Clocking
- Single clock synchronous design with a number of switchable clock domains for efficient power usage
Compliance
- FIPS 197
- NIST CAVP (to be used in a FIPS 140-3 compliant product)
- NIST SP800-38A: AES-CTR
- NIST SP800-38E: AES-GMAC, AES-GCM



