IME-IP-340 Inline Memory Encryption Engine
Home > Security IP > Inline Memory Encryption IP > IME-IP-340 Inline Memory Encryption Engine
IME-IP-340 Inline Memory Encryption (IME) Engine provides just-in-time encryption, decryption and authentication for all memory read and write requests between a host processor and its attached memory. Absent encryption, instruction and data stored in external memory are vulnerable to attack, introspection, or modification as they are loaded and executed.
Historically, inline memory encryption’s performance impact was too great to justify implementation. However, the growing threat environment has raised the stakes for protecting memory data transactions. The Rambus IME-IP-340 Engine mitigates physical attack vectors and does so with high throughput and low latency to make memory encryption viable and practicable.
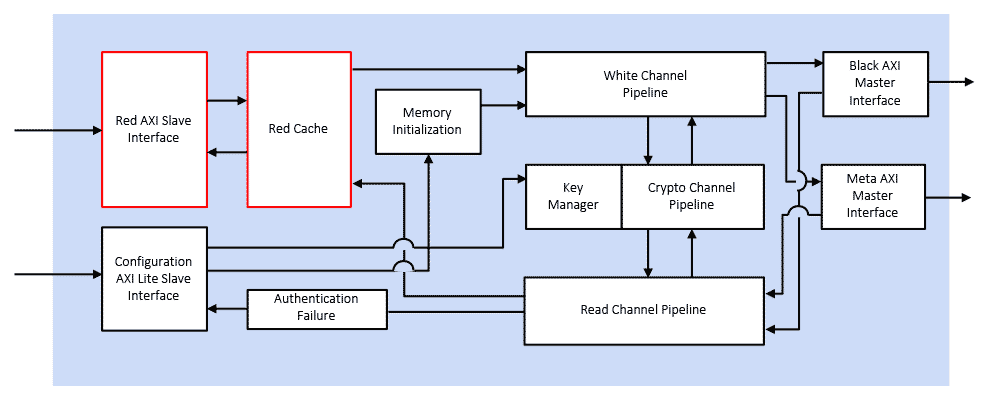
How the IME-IP-340 Engine Works
The Rambus IME-IP-340 Engine provides encryption, decryption and authentication for all memory read and write requests between a host processor and its attached memory. The IME-IP-340 Engine is instantiated on the host (SoC or FPGA) between the processor logic and the memory controller. The IME-IP-340 Engine is a high-throughput, low latency, military-grade security solution. Its features can be configured at compile and/or runtime.
Introduction to Side-Channel Attacks
Side-channel attacks, including simple power analysis and differential power analysis, conducted against electronic gear are relatively simple and inexpensive to execute. An attacker does not need to know specific implementation details of the cryptographic device to perform these attacks and extract keys. As all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.
Deep Anti-Tamper Experience
As the inventor and pioneer of DPA and an acknowledged leader in device security, Rambus is uniquely qualified to provide anti-tamper solutions for the most stringent requirements. Rambus technologies protect more than 9 billion chips per year, and as a US-based, independent company, Rambus has the experience and pedigree to be the solution provider of choice. Rambus has for more than 20 years supplied solutions for government and defense applications, including anti-tamper cores, software libraries, and testing workstations.
MACsec Fundamentals
For end-to-end security of data, it must be secured both when at rest (stored on a connected device) and when in motion (communicated between connected devices). For data at rest, a hardware root of trust anchored in silicon provides that foundation upon which all device security is built. Similarly, MACsec security anchored in hardware at the foundational communication layer (Layer 2) provides that basis of trust for data in motion over Ethernet-based networks.Solution Offerings
- Performs encryption, decryption and/or authentication using AES Counter Mode (CTR) or Galois Counter Mode (GCM)
- Supports AES key sizes 128 or 256
- Internal key management with NIST-compliant key generation
- Encrypt memory space into user-defined vaults, each with a unique key
- Compatible with AMBA AXI4 interface
- Supports hard or soft memory controllers in Xilinx FPGA and SoC devices
- Supports multiprocessor systems
- Supports modern operating systems with and without MMUs
- Robust Side Channel Attack (SCA), Differential Power Analysis (DPA) countermeasures
- Implemented in Xilinx ZU, ZU+ and Versal. Ready for implementation in other FPGA platforms
- FPGA resources used: 25K-120K LUTs depending on configuration
- Low application performance impact: 1-6% depending on configuration
- Low memory overhead: ~10-20% of available memory addresses used for overhead; zero system memory overhead is possible using metadata on a separate bus
- User configurable
- Error handling via IRQ output and separate AXI interface
- Driver with API for programming entropy (user defined)
- Automatic key generation and storage (once entropy is initialized)
- Xilinx IP-XACT Package (VHDL)
- Product Documentation
- Example design with tutorial
- Simulation test bench
- Technical support




