Home > Security IP > Root of Trust Solutions > RT-64x Embedded HSM Family (Root of Trust)
The Rambus RT-64x Embedded Hardware Security Module (Root of Trust) family are fully programmable, ISO 26262 ASIL-B and ASIL-D hardware security cores offering security by design for automotive applications. They protect against a wide range of failures such as permanent, transient and latent faults and hardware and software attacks with state-of-the-art anti-tamper and security techniques.
As the connected nature of automobiles evolves, device architects face a growing array of emerging security threats. Whether V2X, ADAS, infotainment, or other application, one constant in automotive design is the need for an embedded hardware security module-based security implementation. The Rambus RT-640 is the ideal security co-processor for automotive uses. Built on a custom 32-bit RISC-V siloed and layered secure co-processor, along with dedicated secure memories, the RT-640 features a number of high-capability cryptographic accelerators like AES (all modes), HMAC-SHA-2 (all modes), RSA up to 4096 bits, ECC up to 521 bits, a NIST-compliant Random Bit Generator, and Fast DMA capability.
The RT-640 is certified by TÜV-SGS as ISO-26262 ASIL-B satisfying the ASIL-B Single Point Fault Metric (SPFM ≥ 90 % of faults detected) and Latent Fault Metric (LFM ≥ 60 % of faults detected). The development process for Rambus Root of Trust products is also certified to ISO-26262. To support customers, the RT-640 package comes with the proper ASIL documentation, such as the ASIL-B Failure Modes Effects and Diagnostic Analysis (FMEDA and Safety manuals).
The RT-641 is ASIL-B compliant and builds on the RT-640 with Chinese cipher algorithms SM2, SM3 and SM4, offering security by design for automotive applications that require Chinese crypto-based security support.
If higher SPFM and LFM rates are required, the RT-645 ASIL-D ready configuration is available. The RT-645 is certified by TÜV-SGS as ISO-26262 ASIL-D ready satisfying the ASIL-D Single Point Fault Metric (SPFM ≥ 99 % of faults detected) and Latent Fault Metric (LFM ≥ 90 % of faults detected). To support customers, the RT-645 package comes with the proper ASIL documentation, such as the ASIL-D Failure Modes Effects and Diagnostic Analysis (FMEDA), Dependent Failure Analysis (DFA) and Safety manuals.
Satisfying use cases such as secure boot, EVITA and SHE+ HSM and AutoSAR functionality, as well as protection of propriety algorithms, the Rambus RT-64x Root of Trust family is ideally suited for automotive applications where security is imperative.
Navigating the Intersection of Safety and Security

Vehicle systems and the semiconductors used within them are some of the most complex electronics seen today. To support the realization of Level 4 and Level 5 (L4/L5) autonomous driving, a massive restructure is underway. The software-defined vehicle, the automotive Ethernet, vehicle-to-everything (V2X) connectivity, and domain controller units are just some of the new technologies required to realize L4/L5 capabilities. Ensuring all these new systems are both functionally safe and secure from cyberattacks is mission critical.
How the Root of Trust Works
The Rambus Root of Trust RT-640 is an independent hardware security core designed for integration into automotive semiconductor devices, offering secure execution of user applications, tamper detection and protection, and secure storage and handling of keys and security assets. The RT-640 implements hardware and software safety mechanisms to exceed ASIL-B safety integrity levels. It offers chipmakers a siloed approach to security; while located on the same silicon as the main processor, the secure processing core is physically separated. A layered security approach enforces access to crypto modules, memory ranges, I/O pins, and other resources, and assures critical keys are available through hardware only with no access by software. While based on a custom processor, the Rambus Root of Trust supports all common main processor architectures, including ARM, RISC-V, x86 and others.
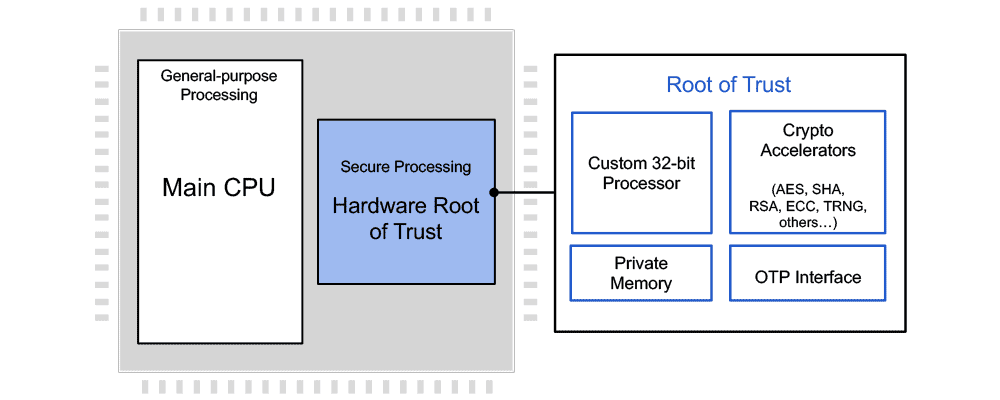
The Root of Trust supports multi-tenant deployments by offering true multiple root of trust capabilities. Each individual Secure Application can be assigned its own unique keys, meaning permissions and access levels are set completely independent of others. Secure Applications are siloed from each other, ensuring the best approach to security. OEMs can determine access levels and permissions for each and all processes operating within the secure processor.
Secure Applications
Included with the RT-64x Hardware Root of Trust cores are a series of standard secure applications (“containers”) to speed development, including secure boot, identity management, HSM reference, and others. Dedicated EVITA-Full and EVITA-Medium Secure Applications can be offered on request. A container development kit (CSDK) is also included to allow the development of custom containers for specific use cases.
Protecting Data and Devices Now and in the Quantum Computing Era

Quantum computing is being pursued across industry, government and academia with tremendous energy and is set to become a reality in the not-so-distant future. Once sufficiently large quantum computers exist, traditional asymmetric cryptographic methods for key exchange and digital signatures will be broken. Many initiatives have been launched throughout the world to develop and deploy new quantum-resistant cryptographic algorithms, known as Post-Quantum Cryptography (PQC).
Solution Offerings
Superior Security
- Hardware Root of Trust cores employing a custom RISC-V secure processor
- RT-640: ASIL-B Certified
- RT-641: ASIL-B Certified with Chinese SM2, SM3 and SM4 algorithm support
- RT-645: ASIL-D Certified
- Hardware and software safety mechanisms to exceed ASIL-B/ASIL-D safety integrity levels
- Secure in-core processing and industry-leading anti-tamper protections
- Multi-layered security model provides protection of all components in the core
- NIST CAVP and CMVP compliant for FIPS 140-2 validation
Enhanced Flexibility
- 3rd-party applications run securely within trusted boundary, each with its own assigned security permissions
- Complete development environment allows OEMs and users to easily develop secure applications (”containers”); standard use case application containers provided
- Support for secure provisioning of keys and firmware at manufacturing or in the field
- Support for multiple roots of trust within a single secure core
Security Models
- Hierarchical privilege
- Secure key management policy
- Hardware-enforced isolation/access control/protection
- Error management policy
Cryptographic Accelerators
- Includes AES, HMAC, RSA, ECC, RBG (configuration-dependent)
Security Modules
- Canary logic for protection against glitching and overclocking
- Secure key derivation and key transport
- Life cycle management
- Secure test and debug
- Feature management
- Hardware integration guide
- Hardware and software reference manuals
- Programming guides
- ASIL-B/ASIL-D FMEDA and Safety Manual
Tools and Scripts
- Verilog for synthesis and simulation
- All scripts and support files needed for standard EDA tool flows integration deliverables
Integration Deliverables
- Complete verification test bench and comprehensive set of test vectors
- Container-authoring software
- Boot loader and firmware, including secure RTOS and security monitor
- HLOS APIs for accessing capabilities
- Complete development environment, including compiler, assembler, debugger, simulator, reference code
Secure Applications
| Secure Application | Description |
|---|---|
| Linux Secure Boot | Implements secure boot for Linux OS, secured by the Root of Trust co-processor |
| Linux Secure FOTA | Implements secure Firmware Over the Air (FOTA) updates for Linux OS |
| Secure Boot | Uses the Root of Trust co-processor to assist in the secure boot process of ASICs and FPGAs |
| Secure Data Storage | Uses the Root of Trust co-processor to protect user credentials or biometric templates |
| Open SSL Hardening | Hardens the OpenSSL crypto operations via the Root of Trust secure co-processor |
| Reference HSM | Implements a basic HSM supporting AES, HMAC, SHA256, ECDSA, X.509 certificates and secure storage |
| Unique ID Generator | Creates a Root of Trust unique ID and stores it in the Root of Trust NVM (Non Volatile Memory) |



