Many electronic devices that use cryptography are susceptible to side channel attacks. These low-cost, non-invasive methods enable attackers to extract the secret cryptographic keys used during normal device operations by monitoring a device’s timing, power consumption, or electromagnetic emissions. Side channel attacks leave no trace, and can often be performed quickly using consumer-level equipment. Once the secret keys have been extracted, attackers can gain unauthorized access, decrypt or forge messages, steal identities, clone devices, create unauthorized signatures, and perform other unauthorized transactions. DPA Countermeasures are fundamental techniques developed to protect against side channel attacks—safeguarding billions of devices from unauthorized use and access.
- Superior protection against side channel attacks
- Simplified device testing for power analysis vulnerabilities
What are DPA Countermeasures?
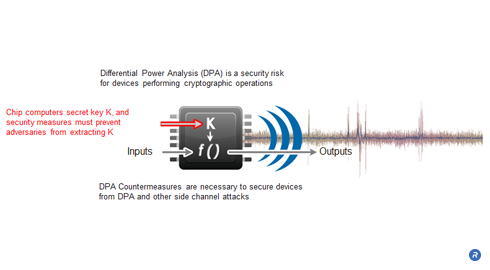
Simple Power Analysis (SPA) and Differential Power Analysis (DPA) are powerful, non-invasive side channel attacks that allow adversaries to compromise the security of tamper-resistant devices by analyzing their power consumption. SPA recovers secret keys through direct observation of a device’s power consumption, while DPA attacks employ statistical techniques to extract secret key information from multiple power consumption measurements. DPA can extract secret keys in a noisy environment where the power consumption of the cryptographic computation is a very small fraction of the overall power consumption of a system. DPA Countermeasures were developed to protect tamper-resistant devices against side channel attacks including SPA, DPA and related electromagnetic (EM) attacks.
DPA Countermeasures consist of a broad range of software, hardware, and protocol techniques that protect tamper-resistant devices from side channel attacks in a number of ways including:
- Leak reduction – reducing information leaked into the side channel to decrease signal-to-noise (S/N) ratios
- Amplitude and temporal noise – adding amplitude or temporal noise into the side channel to decrease S/N ratio
- Balanced hardware and software – using hardware and software-based techniques to represent and process data in ways designed to minimize observable data-dependent variations within the side channel
- Incorporating randomness – representing cryptographic intermediates in forms that incorporate unpredictable information to reduce correlation between side channels and the original intermediates
- Protocol-level countermeasures – modifying cryptographic protocols using key update mechanisms to limit the amount of side channel information available to an attacker for any particular key
Who Benefits?
Device and system manufacturers, and end users benefit from the high-levels of security that are provided at the hardware level to protect against side channel attacks. Devices and industries that benefit from DPA Countermeasures include telecommunications, payments and banking, entertainment, pay television, government and defense, mobile devices, automotive, smart cards, media storage and integrated circuits.
