Smart Cities: Threat and Countermeasures
Billions of connected ‘things’ are deployed in smart cities around the world. The rise of the Internet of Things (IoT) exposes a wide range of vulnerabilities that can be exploited by cyber criminals and other malicious actors. Although smart cities are designed to increase productivity and efficiency, they can potentially present serious risks for residents and authorities when cyber security is neglected. There are an unknown number of potential vulnerabilities and methodologies, some of the most common attacks include:
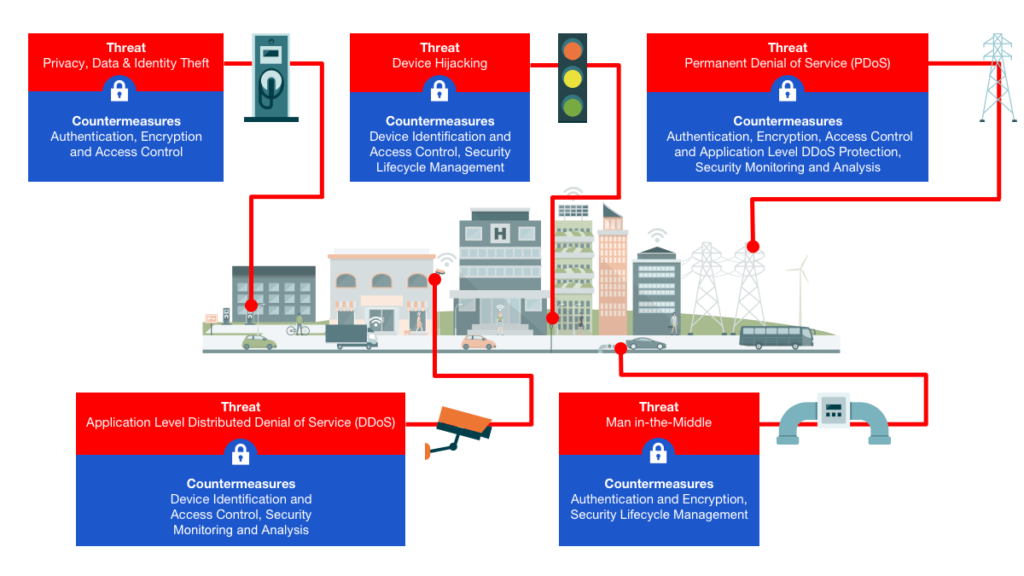
Man-in-the-middle: An attacker breaches, interrupts or spoofs communications between two systems. For example, a man-in-the-middle attack on a smart valve in a wastewater system could be used to cause a biohazard spill.
Data and identity theft: Data generated by unprotected smart city infrastructure such as parking garages, EV charging stations and surveillance feeds provide cyber attackers with an ample amount of targeted personal information that can potentially be exploited for fraudulent transactions and identify theft.
Device hijacking: The attacker hijacks and effectively assumes control of a device. These attacks can be difficult to detect because in many cases, the attacker does not alter the basic functionality of the device. In the context of a smart city, a cyber-criminal could exploit hijacked smart meters to launch ransomware attacks on Energy Management Systems (EMS) or stealthily siphon energy from a municipality.
Distributed Denial of Service (DDoS): A denial-of- service attack (DoS attack) attempts to render a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. This is typically achieved by flooding the target with superfluous requests to prevent legitimate requests from being fulfilled. In the case of a distributed denial-of-service attack (DDoS attack), incoming traffic flooding a target originates from multiple sources, making it difficult to stop the cyber offensive by simply blocking a single source. Within smart cities, a plethora of devices, such as parking meters, can be breached and forced to join a botnet programmed to overwhelm a system by requesting a service simultaneously.
Permanent Denial of Service (PDoS): Permanent denial- of-service attacks (PDoS), also known loosely as phlashing, is an attack that damages the device so badly that it requires replacement or reinstallation of hardware. In a smart city scenario, a hijacked parking meter could also fall victim to sabotage and would have to be replaced.
Securing Smart Cities
Connected smart city devices should be protected by comprehensive IoT security solutions (device to cloud). Practical and simple, yet secure, solutions that can be easily and widely adopted by OEMs and services are more effective than a ‘super solution’ that fails to gain serious traction. Such solutions should include the following capabilities:

Firmware integrity and secure boot
Secure boot utilizes cryptographic code signing techniques, ensuring that a device only executes code generated by the device OEM or another trusted party. Use of secure boot technology prevents hackers from replacing firmware with malicious versions, thereby preventing attacks. Unfortunately, not all IoT chipsets are equipped with secure boot capabilities. In such a scenario, it is important to ensure that the IoT device can only communicate with authorized services to avoid the risk of replacing firmware with malicious instruction sets.
Mutual authentication
Every time a smart city device connects to the network it should be authenticated prior to receiving or transmitting data. This ensures that the data originates from a legitimate device and not a fraudulent source. Secure, mutual authentication— where two entities (device and service) must prove their identity to each other—helps protect against malicious attacks.
Security monitoring and analysis
Captures data on the overall state of the system, including endpoint devices and connectivity traffic. This data is then analyzed to detect possible security violations or potential system threats. Once detected, a broad range of actions formulated in the context of an overall system security policy should be executed, such as quarantining devices based on anomalous behavior.

Security lifecycle management
The lifecycle management feature allows service providers and OEMs to control the security aspects of IoT devices when in operation. Rapid over the air (OTA) device key(s) replacement during cyber disaster recovery ensures minimal service disruption. In addition, secure device decommissioning ensures that scrapped devices will not be repurposed and exploited to connect to a service without authorization.
Rambus Security Solutions for Smart Cities
Root of Trust solutions provide the hardware-level foundation for security enabling functions such as secure boot, secure execution of applications, tamper detection and protection, and secure storage and handling of keys.
Protocol Engines secure network communications between IIOT devices and the cloud without altering the traffic. They enable secure end-to-end communications while maintaining vital network performance.
Provisioning and Key Management secure supply chain solutions for chip and IoT device manufacturers enable secure key insertion and cloud-based device key management services.
