Smart Home: Threats and Countermeasures
An estimated 80% of IoT devices are vulnerable to a wide range of attacks. Clearly, connecting traditionally ‘stand-alone’ smart devices such as lights, appliances and locks introduces numerous cyber security risks. Even connected baby monitors are vulnerable to digital intruders, as a number of horrified parents belatedly discovered when hackers spoke to their young children via compromised devices. Common cyber security threats and attacks against smart home devices include:
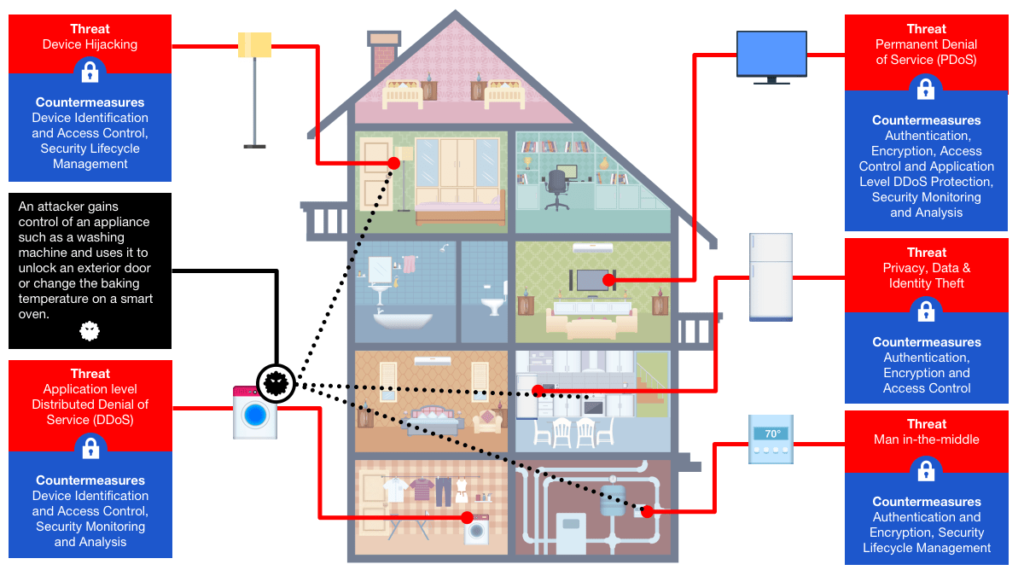
Man-in-the-middle: An attacker breaches, interrupts or spoofs communications between two systems. For example, fake temperature data ‘generated’ by an environmental monitoring device can be spoofed and forwarded to the cloud. Similarly, an attacker can disable vulnerable HVAC systems during a heat wave, creating a disastrous scenario for service providers with affected models.
Data and identity theft: Data generated by unprotected wearables and smart appliances provide cyber attackers with an ample amount of targeted personal information that can potentially be exploited for fraudulent transactions and identify theft.
Device hijacking: The attacker hijacks and effectively assumes control of a device. These attacks are quite difficult to detect because the attacker does not change the basic functionality of the device. Moreover, it only takes one device to potentially re-infect all smart devices in the home. For example, an attacker who initially compromises a thermostat can theoretically gain access to an entire network and remotely unlock a door or change the keypad PIN code to restrict entry.
Distributed Denial of Service (DDoS): A denial-of-service attack (DoS attack) attempts to render a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. In the case of a distributed denial-of-service attack (DDoS), incoming traffic flooding a target originates from multiple sources, making it difficult to stop the cyber offensive by simply blocking a single source. In fact, DDoS attacks are rising rapidly, primarily due to the lack of security in IoT Devices. The Mirai botnet attack was a massive distributed DDoS attack that left much of the internet inaccessible on the US east coast.
Permanent Denial of Service (PDoS):Permanent denial-of-service attacks (PDoS), also known as phlashing, is an attack that damages the device so badly that it requires replacement or reinstallation of hardware. BrickerBot, coded to exploit hard-coded passwords in IoT devices and cause permanent denial of service, is one such example. Another example could see fake data fed to thermostats in an attempt to cause irreparable damage via extreme overheating.
Securing Smart Homes
Connected smart home devices should be protected by a comprehensive IoT security solution (device to cloud) that does not disrupt a Service provider or OEMs profitability or time to market. A comprehensive IoT security solution should include the following capabilities:

Secure boot
Secure boot utilizes cryptographic code signing techniques, ensuring that a device only executes code generated by the device OEM or another trusted party. Use of secure boot technology prevents hackers from replacing firmware with malicious versions, thereby preventing attacks.
Mutual authentication
Every time a smart home device connects to the network it should be authenticated prior to receiving or transmitting data. This ensures that the data originates from a legitimate device and not a fraudulent source. Cryptographic algorithms involving symmetric keys or asymmetric keys can be utilized for two-way authentication. This ensures that the data originates from a legitimate device and not a fraudulent source. Cryptographic algorithms involving symmetric keys or asymmetric keys can be utilized for two-way authentication. For example, the Secure Hash Algorithm (SHA-x) can be used for symmetric keys and the Elliptic Curve Digital Signature Algorithm (ECDSA) for asymmetric keys.

Secure communication (Encryption)
Protecting data in transit between a device and its service infrastructure (the cloud). Encryption ensures that only those with a secret decryption key can access transmitted data. For example, a smart thermostat that sends usage data to the service operator must be able to protect information from digital eavesdropping.

Security monitoring and analysis
Captures data on the overall state of the system, including endpoint devices and connectivity traffic. This data is then analyzed to detect possible security violations or potential system threats. Once detected, a broad range of actions formulated in the context of an overall system security policy should be executed, such as quarantining devices based on anomalous behavior. This monitor-analyze-act cycle may execute in real time or at a later date to identify usage patterns and detect potential attack scenarios. It is critical to ensure that endpoints devices are secured from possible tampering and data manipulation, which could result in the incorrect reporting of events.

Security lifecycle management
The lifecycle management feature allows service providers and OEMs to control the security aspects of IoT devices when in operation. Rapid over the air (OTA) device key(s) replacement during cyber disaster recovery ensures minimal service disruption. In addition, secure device decommissioning ensures that scrapped devices will not be repurposed and exploited to connect to a service without authorization.
Rambus Security Solutions for Smart Home IoT Devices
Root of Trust solutions provide the hardware-level foundation for security enabling functions such as secure boot, secure execution of applications, tamper detection and protection, and secure storage and handling of keys.
Provisioning and Key Management secure supply chain solutions for chip and IoT device manufacturers enable secure key insertion and cloud-based device key management services.
