ICE-IP-339 Inline Cipher Engine with AXI
Home > Security IP > Inline Memory Encryption IP > ICE-IP-339 Inline Cipher Engine with AXI
Modern computing architectures must address increasing concerns regarding off-chip data confidentiality. Key drivers for these concerns are data privacy for attacks with physical access to memory, confidential computing using zero trust computing architectures, regulatory frameworks, and secure encrypted resource virtualization e.g., multi-tenancy support among others.
Inline memory encryption (IME) is a key enabler for protecting data that is stored in off-chip memory (typically, DDR memory). This is also referred to as protection of “data-in-use.” The low latency encryption and decryption is handled by an IME engine with the required cryptographic primitives in the data path connected to off-chip memory via the on-chip memory controller.
The Rambus ICE-IP-339 Inline Cipher Engine can be seamlessly integrated into a customer’s system-on-chip (SOC) to address security and privacy concerns of data-in-use in DDR memory.
The ICE-IP-339 provides an AXI-4 compliant wrapper around the industry-proven Rambus ICE-IP-338 (inline cipher engine). This allows the ICE-IP-339 to act as a transparent data processing pipeline on the read and write AXI data channels. At its heart, it is an encryption/decryption engine deploying AES/SM4-XTS cryptographic primitives. Address information is snooped from the read and write address channels as input for AES-XTS tweak generation. Cryptographic processing is done on the incoming data using the precomputed tweak and the respective key for the required operation based on the data direction.
The ICE-IP-339 supports compliance with the FIPS-197, IEEE-P1619/D16, and NIST-SP800-38E standards, supporting AES-XTS (and optionally SM4-XTS) with 128 and 256-bit keys. The ICE-IP-339 is delivered with fully verified parameterized RTL, directed testbenches and UVM verification environment.

Secure Networking Basics: MACsec, IPsec, and SSL/TLS/DTLS
The MACsec, IPsec and SSL/TLS/DTLS protocols are the primary means of securing data in motion (communicated between connected devices). These protocols can be anchored in hardware or implemented in software as part of an end-to-end security architecture. This white paper provides fundamental information on each of these protocols including their interrelationships and use cases.How the ICE Engine Works
At startup, the ICE-IP-339 engine receives ephemeral key from the SoC, which it autonomously converts into appropriate keys for encryption and decryption.
The ICE-IP-339 engine snoops information from the AXI4 address channels and transparently converts them into tweak computation inputs for the cryptography engine. It does this by arbitrating over the read and write address channels.
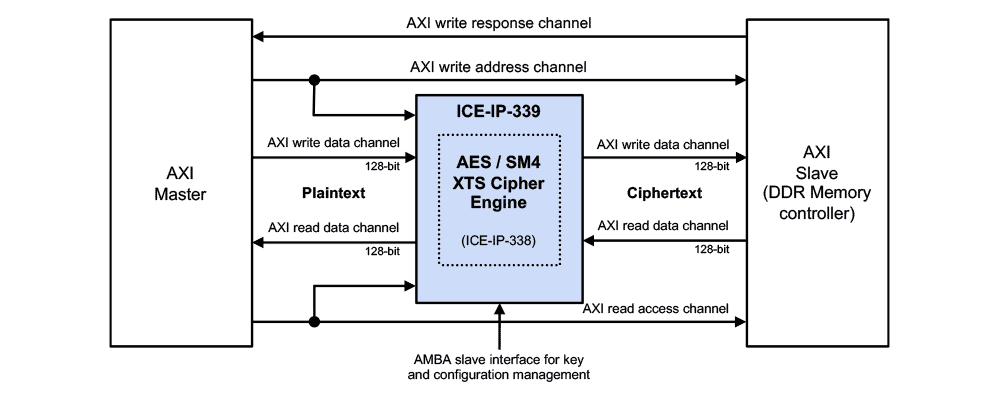
When data is input, appropriate cryptographic operation is employed by the cryptography-engine. This is done by arbitrating over the read and write 128-bit data channels. SoC read-data from the DDR controller implies decryption, write-data from the AXI-master implies encryption. The ICE-IP-339 assumes XTS sector sizes of 64 Byte (= cache line width) and 16 Byte data access granularity.
The ICE-IP-339 engine acts as an AXI-to-AXI wedge in between the SoC AXI bus fabric, and the DDR memory controller operating as an AXI slave. It supports standard AMBA interfaces (AXI4 for datapath and AMBA (APB) interface for key management), thereby, enabling seamless integration with standard SoC components. The internals of the IP (such as command and data buffering) can be configured as required by the SoC. Furthermore, the debug support signals facilitate transparency into internal data flow, thereby, simplifying the overall integration and verification of overall system.
MACsec Fundamentals
For end-to-end security of data, it must be secured both when at rest (stored on a connected device) and when in motion (communicated between connected devices). For data at rest, a hardware root of trust anchored in silicon provides that foundation upon which all device security is built. Similarly, MACsec security anchored in hardware at the foundational communication layer (Layer 2) provides that basis of trust for data in motion over Ethernet-based networks.Solution Offerings
Performance
- Throughput: 128 bit (16 Byte) wide encryption/decryption per cycle
- Throughput: 1 tweak computation per 4 clock cycles
- Bidirectional design including arbitration between read and write requests
- Zero clock overhead for switching between encryption (write) and decryption (read)
- 30-40 cycle data channel latency
Cryptographic Processing
- Algorithms: AES or AES and SM4
- Modes of operation: XTS
- Supported key sizes: 128 and 256 bits
PPA1
- >1GHz max clock frequency
- Area: 50k RefGates excluding area of internal crypto engine
- Power: 0.2-0.4mW/MHz/16B(block)
1Reference Technology: TSMC 16nm, LVT
Interface
- AMBA AXI4 complaint 128-bit data and 32-bit address channel interface (for Master and Slave integration)
- AMBA APB complaint 32-bit control interface
- Interrupts and internal buffer status flags
- Debug and internal errors including (optional) ECC for internal SRAMs of crypto engine
- Zeroization and reset
Compliance
- FIPS 197, IEEE-P1619/D16
- NIST CAVP (to be used in a FIPS 140-3 compliant product)
- NIST SP800-38E: AES-XTS
Packages
- RTL IP
- Driver development kit
Complete Documentation
- Hardware integration guide
- Hardware reference manual
Tools and Scripts
- Verilog for synthesis and simulation
- All scripts and support files needed for standard EDA tool flows
Integration Support
- Complete verification test bench
- Comprehensive set of test vectors



