Home > Security IP > Security Response Center > Security Advisories > SafeZone Basic Crypto Module, non-FIPS certified version
Rambus Security Vulnerability Disclosure: SafeZone Basic Crypto Module, non-FIPS certified version
Publish Date: March 1, 2022
Rambus Vulnerability ID: RMBS-2021-01
Background
The SafeZone Crypto Libraries were developed by Inside Secure and were acquired by Rambus as part of an acquisition from Verimatrix. There were both FIPS-certified and non-FIPS-certified versions of the SafeZone crypto libraries. The standalone non-FIPS-certified offering had been discontinued for new licenses, but Rambus continues to support existing customers of this product.
A security vulnerability has been identified in the non-FIPS-certified version of the crypto library in SafeZone as described below. A patch which remediates the vulnerability is available and has been distributed to existing customers that are affected by the vulnerability.
“SafeZone” Product Status
| Product Name (Crypto Module) | Affected by Vulnerability | Affected Versions | Available for Licensing | Patch Available |
| SafeZone Crypto Libraries (Basic Crypto Module, non-FIPS certified) | Yes | 9.3.x, 10.0.x, 10.1.x, 10.2.x, 10.3.x | No | Yes, all versions; Also as part of SafeZone 10.4.0 |
| FIPS Security Toolkit* (FIPS 140-2 SW Crypto Module v1.2) | No | None | Yes | N/A |
| FIPS Security Toolkit* (FIPS 140-3 SW Crypto Module v2.0) | No | None | Yes | N/A |
*SafeZone FIPS-certified versions are now offered as “FIPS Security Toolkit” by Rambus
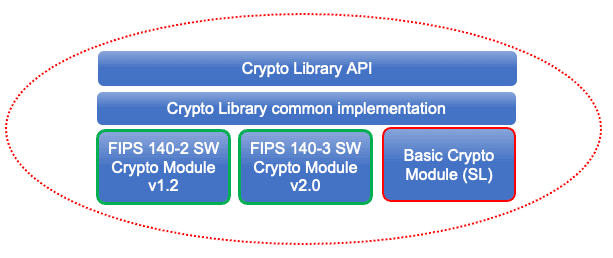
Figure 1. Only the SafeZone Basic Crypto Module is affected by the security vulnerability
Vulnerability Description
The speed-optimized, multi-threaded version of the RSA key generation function CLS_PK_KeyGenMT( ) used in the non-FIPS Basic Crypto Module may create weak RSA keys.
The vulnerability does not exist in the single-threaded version of the RSA key generation function CLS_PK_KeyGen_RSA( ).
Impact
The distance between the p and q values of the generated RSA key may not be sufficient which makes the key vulnerable to factorization attacks.
Affected Versions
SafeZone Crypto Libraries (Basic Crypto Module) versions: 9.3.x, 10.0.x, 10.1.x, 10.2.x, 10.3.x. the last update of version 10.3.x was June 2020.
Unaffected Versions
FIPS 140-2 and FIPS 140-3 SW Crypto Modules are unaffected.
SafeZone Crypto Libraries (Basic Crypto Module) versions: 10.4.0 is unaffected.
Remediation
Rambus provided a patch for all affected versions that modifies the CLS_PK_KeyGenMT( ) implementation in a way that ensures the distance between the p and q values is sufficient.
Action Taken
A customer notified Rambus of this issue on November 2, 2021. Rambus developed a patch and provided it to the affected customer within two weeks.
All other Rambus customers that may use the affected crypto library were provided with a patch on or before December 15, 2021.
More recently an ‘advisory message’ was provided to SafeZone customers with access to the Crypto Libraries to confirm that they are not affected by this vulnerability.
Acknowledgement
The vulnerability was found in a Rambus customer product. The vulnerability was reported to the customer by independent security researcher, Hanno Böck, who was referred to the Rambus Security IP team.
For any inquiries, please contact Rambus.
