[Last updated on April 8, 2025] A root of trust is the security foundation for an SoC, other semiconductor device or electronic system. However, its meaning differs depending on who you ask. From our perspective, the hardware root of trust contains the keys for cryptographic functions and is usually a part of the secure boot process providing the foundation for the software chain of trust.
In this article:
-
- What is hardware root of trust?
- What are the types of a silicon-based hardware root of trust?
- What are the benefits of a programmable hardware root of trust?
- What features should a programmable hardware root of trust offer?
- What is the Rambus Root of Trust?
- How is the Rambus Root of Trust architected for security?
- What’s new in the latest generation of Rambus Root of Trust IP?
- What is Quantum Safe Cryptography?
- Is there a Root of Trust configured for my application?
- What should I keep in mind when selecting a Root of Trust IP?
What is hardware root of trust?
A hardware root of trust is the foundation on which all secure operations of a computing system depend. It contains the keys used for cryptographic functions and enables a secure boot process. It is inherently trusted and therefore must be secure by design. The most secure implementation of a root of trust is in hardware making it immune from malware attacks. As such, it can be a stand-alone security module or implemented as security module within a processor or system on chip (SoC).
What are the types of a silicon-based hardware root of trust?
A silicon-based hardware root of trust falls into two categories: fixed function and programmable. Essentially, a fixed-function root of trust is firmware controlled. These are typically compact and designed to perform a specific set of functions like data encryption, certificate validation and key management. These compact, firmware-controlled root of trust solutions are particularly well suited for Internet of Things (IoT) devices.
In contrast, a hardware-based programmable root of trust is built around a CPU. Performing all the functions of a firmware-controlled solution, a programmable root of trust can also execute a more complex set of security functions. A programmable root of trust is versatile and upgradable, enabling it to run entirely new cryptographic algorithms and secure applications to meet evolving attack vectors.
What are the benefits of a programmable hardware root of trust?
The cybersecurity threat landscape is dynamic and rapidly evolving. Indeed, attackers are constantly finding new ways to exploit critical vulnerabilities across a wide range of applications and devices. Fortunately, a programmable hardware-based root of trust can be continuously updated to contend with an ever-increasing range of threats.
A programmable hardware-based root of trust is a key component to protect against a number of security threats, including:
- Host processor compromise
- Non-volatile memory (NVM) key extraction
- Tearing and other attacks against NVM writes
- Corruption of non-volatile memory or fuses
- Test and debug interface attacks
- Side-channel and perturbation attacks including Simple Power Analysis (SPA), Differential Power Analysis (DPA) and Fault Injection Attacks (FIA)
- Manufacturing/personalization facility compromise (insider attack)
- Man-in-the-middle and replay attacks
- Probing of external buses
What features should a programmable hardware root of trust offer?
A programmable hardware root of trust should be purpose-built; specifically designed from the ground up to provide a robust level of security. Since the root of trust is a logical target for an attacker, it should be made as secure as possible to safeguard it from compromise. Capabilities should include:
-
-
Siloed Execution:
Ensures that sensitive security functions are only performed within a dedicated security domain that is physically separated from the general-purpose processor. This paradigm allows the primary CPU to be optimized for architectural complexity and performance – with security functionality safely isolated in a physically separated root of trust.
-
Comprehensive Anti-Tamper and Side-Channel Resistance:
Protects against multiple fault injection and side-channel attacks.
-
Layered Security:
Provides multiple layers of robust defense to avoid a single point of failure. Access to cryptographic hardware modules and other sensitive security resources are enforced in hardware, while critical keys are only available to hardware. Software security can be layered on top of a hardware-based root of trust, thereby providing additional flexibility and security.
-
Multiple Root of Trust Instances:
Ensures isolation of resources, keys and security assets. In real-world terms, this means each entity – such as a chip vendor, OEM or service provider – has access to its own ‘virtual’ security core and performs secure functions without having to ‘trust’ other entities. This allows individual entities to possess unique root and derived keys, as well as access only to specified features and resources such as OTP, debug and control bits. Moreover, support for multiple root of trust instances enables the security core to assign or delegate permissions to other entities at any point in the device life cycle, while isolating (in hardware) unique signed apps that are siloed away from other programs.
-
What is the Rambus Root of Trust?
Rambus offers a catalog of robust Root of Trust solutions, ranging from richly featured military-grade co-processors to highly compact firmware-controlled. With a breadth of solutions applicable from the data center to IoT devices, Rambus has a Root of Trust solution for almost every application.
Rambus’ Parvez Shaik explains the importance of addressing supply chain vulnerabilities, the advantages of a hardware root of trust, and the new features of the third-generation CryptoManager Root of Trust products in this episode of Ask the Experts.
Jump to: Root of Trust solutions »
How is the Rambus Root of Trust architected for security?
The CryptoManager RT-6xx Root of Trust family from Rambus is the latest generation of fully programmable FIPS 140-3 compliant hardware security cores offering Quantum Safe security by design for data center and other highly secure applications. The CryptoManager RT-6xx family protects against a wide range of hardware and software attacks through state-of-the-art side channel attack countermeasures and anti-tamper and security techniques.
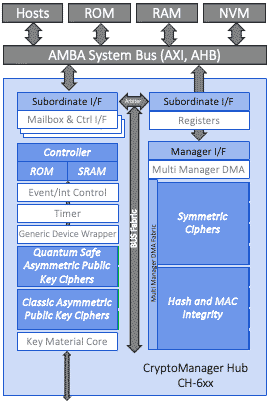
CryptoManager RT-6xx Series Root of Trust Block Diagram
The diagram above illustrates the basic architecture of the Rambus RT-600 series Root of Trust, including:
The CryptoManager RT-6xx Root of Trust is a siloed hardware security IP core for integration into semiconductors, offering secure execution of authenticated user applications, tamper detection and protection, secure storage and handling of keys and security assets, and optional resistance to side-channel attacks. The Root of Trust is easily integrated with industry-standard interfaces and system architectures and includes standard hardware cryptographic cores. Access to crypto modules, keys, memory ranges, I/O, and other resources is enforced in hardware. Critical operations, including key derivation and storage, are performed in hardware with no access by software. The Root of Trust is based on a custom 32-bit processor designed specifically to provide a trusted foundation for secure processing on chip and in the system.
The Root of Trust supports all common host processor architectures including ARM, RISC-V, x86 and others. The multi-threaded secure processor runs customer developed signed code either as a monolithic supervisor or as loadable security applications which include permissions and security-related metadata. It can implement standard security functionality provided by Rambus, or complete customer-specific security applications, including key and data provisioning, security protocols, biometric applications, secure boot, secure firmware update, and many more.
Keep on reading:
Rambus CryptoManager Root of Trust Solutions Tailor Security Capabilities to Specific Customer Needs with New Three-Tier Architecture
What is Quantum Safe Cryptography?
The CryptoManager RT-6xx Root of Trust series is at the forefront of a new category of programmable hardware-based security cores with its new Quantum Safe Cryptography features.
Once sufficiently powerful quantum computers exist, traditional asymmetric cryptographic methods for key exchange and digital signatures will be easily broken. New cryptographic algorithms known as quantum safe cryptography (QSC) or post-quantum cryptography (PQC) are needed to protect against quantum computer attacks.
The latest generation of Rambus Root of Trust IP offers a state-of-the-art programmable security solution to protect hardware and data with NIST and CNSA quantum-resistant algorithms. The Quantum Safe Engine operates with the CRYSTALS-Kyber and CRYSTALS-Dilithium algorithms, as well as the stateful hash-based signature schemes XMSS (eXtended Merkle Signature Scheme) or LMS (Leighton-Micali Signatures).
Learn more about Quantum Safe Cryptography:
– Post-quantum Cryptography (PQC): New Algorithms for a New Era
– Rambus Expands Quantum Safe Solutions with Quantum Safe Engine IP
Is there a Rambus Root of Trust configured for my application?
There are Rambus Root of Trust solutions tailored to address the specific security requirements and certification standards of nearly every application:
-
- The RT-1xx series of Root of Trust solutions are designed for use in power and space-constrained applications as in IoT devices. Featuring a firmware-controlled architecture with dedicated secure memories, the RT-1xx hardware Root of Trust cores provide a variety of cryptographic accelerators including AES, SHA-2, RSA and ECC. There are versions which include SM2, SM3 and SM4 accelerators for the China market.
- The CryptoManager RT-6xx is a fully programmable, FIPS 140-3 compliant, hardware security core offering security-by-design for data center cloud, AI/ML, as well as general purpose semiconductor applications. It protects against a wide range of hardware and software attacks through state-of-the-art anti-tamper and security techniques.
- The CryptoManager RT-7xx is tailored for the automotive market offering ISO 26262 and ISO 21434 compliant hardware security. It supports vehicle-to-vehicle and vehicle-to-infrastructure (V2X), advanced driver-assistance systems (ADAS) and infotainment uses.
- CryptoCell Root of Trust solutions are programmable, FIPS 140-3 certifiable hardware security modules. They are designed to be integrated into Arm TrustZone-based SoCs or FPGAs where power and space are a consideration.
Find out more: See all Rambus Root of Trust IP Solutions »
What should I keep in mind when selecting a Root of Trust IP?
Root of Trust product designs vary greatly in architecture and capabilities. When selecting a Root of Trust solution, it’s important to ask the right questions to ensure the best level of protection for your specific security needs.
Some questions to consider include:
- What is the end use of the chip?
- Who and what are you protecting against?
- What is the risk of a compromised device?
- What certifications are required?
It’s also worth noting that Root of Trust products can be tailored to match an application’s security threat model, use case, industry segment, lifetime, cost, and geography. Some examples of the different criteria that can be selected include the crypto algorithms, security/anti-tamper mechanisms, and provisioning methods used.
Next steps?
If you have any questions about how to select a Root of Trust for your next project, contact us here.
Explore more resources:
– The Ultimate Guide to Secure Silicon: Root of Trust
– Ask the Experts: PUF-based Security
– Implementing State-of-the-Art Digital Protection with Rambus CryptoManager Security IP


Leave a Reply