Last updated on: July 13, 2023 A root of trust is the security foundation for an SoC, other semiconductor device or electronic system. However, its meaning differs depending on who you ask. For example, the hardware root of trust contains the keys for cryptographic functions and is usually a part of the secure boot process providing the foundation for the software chain of trust.
In this article:
-
- What is hardware root of trust?
- What are the types of a silicon-based hardware root of trust?
- What are the benefits of a programmable hardware root of trust?
- What features should a programmable hardware root of trust offer?
- What is the Rambus Root of Trust?
- How is the Rambus Root of Trust architected for security?
- What’s new in the latest generation of Rambus Root of Trust IP?
- What is Quantum Safe Cryptography?
- Is there a Root of Trust configured for my application?
- What should I keep in mind when selecting a Root of Trust IP?
What is hardware root of trust?
A hardware root of trust is the foundation on which all secure operations of a computing system depend. It contains the keys used for cryptographic functions and enables a secure boot process. It is inherently trusted, and therefore must be secure by design. The most secure implementation of a root of trust is in hardware making it immune from malware attacks. As such, it can be a stand-alone security module or implemented as security module within a processor or system on chip (SoC).
What are the types of a silicon-based hardware root of trust?
A silicon-based hardware root of trust falls into two categories: fixed function and programmable. Essentially, a fixed-function root of trust is firmware controlled. These are typically compact and designed to perform a specific set of functions like data encryption, certificate validation and key management. These compact, firmware-controlled root of trust solutions are particularly well suited for Internet of Things (IoT) devices.
In contrast, a hardware-based programmable root of trust is built around a CPU. Performing all the functions of a firmware-controlled solution, a programmable root of trust can also execute a more complex set of security functions. A programmable root of trust is versatile and upgradable, enabling it to run entirely new cryptographic algorithms and secure applications to meet evolving attack vectors.
What are the benefits of a programmable hardware root of trust?
The cybersecurity threat landscape is dynamic and rapidly evolving. Indeed, attackers are constantly finding new ways to exploit critical vulnerabilities across a wide range of applications and devices. Fortunately, a programmable hardware-based root of trust can be continuously updated to contend with an ever-increasing range of threats.
A programmable hardware-based root of trust is a key component to protect against a number of security threats, including:
- Host processor compromise
- Non-volatile memory (NVM) key extraction
- Tearing and other attacks against NVM writes
- Corruption of non-volatile memory or fuses
- Test and debug interface attacks
- Side-channel and perturbation attacks including Simple Power Analysis (SPA), Differential Power Analysis (DPA) and Fault Injection Attacks (FIA)
- Manufacturing/personalization facility compromise (insider attack)
- Man-in-the-middle and replay attacks
- Probing of external buses
What features should a programmable hardware root of trust offer?
A programmable hardware root of trust should be purpose-built; specifically designed from the ground up to provide a robust level of security. Since the root of trust is a logical target for an attacker, it should be made as secure as possible to safeguard it from compromise. Capabilities should include:
-
-
Siloed Execution:
Ensures that sensitive security functions are only performed within a dedicated security domain that is physically separated from the general-purpose processor. This paradigm allows the primary CPU to be optimized for architectural complexity and performance – with security functionality safely isolated in a physically separated root of trust.
-
Comprehensive Anti-Tamper and Side-Channel Resistance:
Protects against multiple fault injection and side-channel attacks.
-
Layered Security:
Provides multiple layers of robust defense to avoid a single point of failure. Access to cryptographic hardware modules and other sensitive security resources are enforced in hardware, while critical keys are only available to hardware. Software security can be layered on top of a hardware-based root of trust, thereby providing additional flexibility and security.
-
Multiple Root of Trust Instances:
Ensures isolation of resources, keys and security assets. In real-world terms, this means each entity – such as a chip vendor, OEM or service provider – has access to its own ‘virtual’ security core and performs secure functions without having to ‘trust’ other entities. This allows individual entities to possess unique root and derived keys, as well as access only to specified features and resources such as OTP, debug and control bits. Moreover, support for multiple root of trust instances enables the security core to assign or delegate permissions to other entities at any point in the device life cycle, while isolating (in hardware) unique signed apps that are siloed away from other programs.
-
What is the Rambus Root of Trust?
Rambus offers a catalog of robust Root of Trust solutions, ranging from richly featured military-grade co-processors to highly compact firmware-controlled. With a breadth of solutions applicable from the data center to IoT devices, Rambus has a Root of Trust solution for almost every application.
Jump to: Root of Trust solutions »
How is the Rambus Root of Trust architected for security?
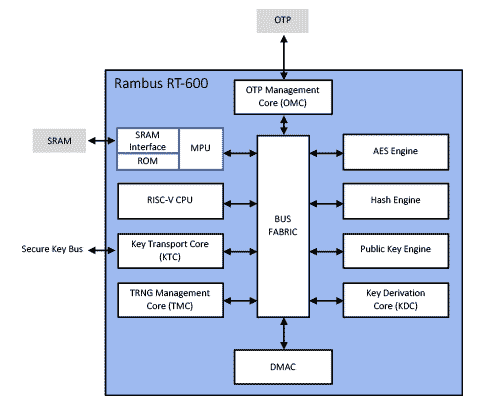
The Rambus RT-600 series of Root of Trust hardware IP cores is built around Verilog RTL, which enables the customizable and modular root of trust to be easily integrated in any chip or FPGA design. Perhaps most importantly, the Rambus RT-600’s layered architecture provides the security of a hardware design with the flexibility of software.
Simplified Rambus RT-600 Series Root of Trust Block Diagram
The diagram above illustrates the basic architecture of the Rambus RT-600 series Root of Trust, including:
-
-
Purpose-built 32-bit CPU:
The CPU is a security optimized, configurable and multistage 32-bit RISC-V processor.
-
Multiple Bus Fabrics:
Connects various hardware modules within the Rambus Root of Trust. Note: There is a single bus that is completely dedicated to transporting and protecting sensitive keys from unauthorized software access.
-
Private SRAM:
Features multiple interfaces and a hardened memory protection unit. The Rambus Root of Trust’s SRAM – which stores secure assets in a memory region isolated from the rest of the system – also includes a small amount of read-only memory.
-
Key Transport Core:
Manages keys that may be used externally.
-
True Random Number Generator:
Generates true random numbers for multiple cryptographic algorithms and protocols.
-
DMA Controller:
Moves data in and out of the core.
-
Key Derivation Core:
Allows multiple keys to be derived for different applications – while keeping keys cryptographically isolated.
-
Cryptographic Engines:
Includes three (by default) cryptographic engines: one for public key algorithms, elliptic curve and RSA; a hash engine; and an AES engine.
-
OTP Management Core:
Manages one-time programmable memory that is used for storing keys and other security assets.
As noted above, the versatile Rambus RT-600 series Root of Trust can be easily integrated into a wide range of silicon. Its standard interfaces include AMBA interface buses for communicating with registers (the control plane interface into the core), as well as an AHB bus that interfaces with system memory (data plane access). The Rambus RT-600 series Root of Trust also offers easy-to-use test interfaces of key buses for supplying keys to external logic, as well as I/O pins for managing various functions like chip features and alerts (controlling and monitoring external logic).
Additional key Rambus Root of Trust security features and capabilities include:
-
Self-Contained Secure Boot Mechanism:
Starts with a first-stage boot ROM that is synthesized into gates.
-
Side-Channel Resistance:
Offers comprehensive protection against various side-channel attacks such as Differential Power Analysis (DPA), Simple Power Analysis (SPA), Simple Electromagnetic Analysis (SEMA), Differential Electromagnetic Analysis (DEMA), Correlation Power Analysis (CPA) and Correlation Electromagnetic Analysis (CEMA). These side-channel countermeasures are present throughout the Rambus Root of Trust, including in the execution pipeline of the CPU itself.
-
Glitch and Fault Injection Attack Protection:
Protects against a full range of glitch and fault injection attacks.
-
Memory Protection Unit:
Locks at boot time and cannot be altered by malicious code.
-
Private SRAM and Isolated CPU Bus:
Prevents modification of the call stack and ensures control flow integrity.
The Rambus RT-600 series Root of Trust – which includes a complete firmware stack – also employs a layered security model for software utilizing privilege levels that are part of the RISC-V ISA. Put simply, these privilege levels are enforced on a hardware level, thereby effectively separating data between their respective layers. More specifically, the least privileged (least secure) layer is the user level, which is where user-written secure applications run. These applications can also be referred to as containers.
The next level is the supervisor level, where a Zephyr-based microkernel customized for security resides and runs. As expected, the highest privilege level is where the most secure code runs, with a security monitor overseeing the microkernel and containers, as well as their interaction with hardware. Although lower levels are more flexible, they are considered less secure. As such, the security monitor is specifically designed to provide a robust level of security protection for the software stack.
What’s new in the latest generation of Rambus Root of Trust IP?
This latest generation of the RT-600 Root of Trust series offers many new features designed to support the security needs of customers today and into the future.
Amongst the new architectural and security features are:
- A AXI4 master interface with 64-bit address
- Caliptra Root of Trust for Measurement (RoTM) with DICE and X.509 support
- A new secure data store mechanism
- A Quantum Safe Engine (QSE) with CRYSTALS-Kyber and CRYSTALS-Dilithium
- Extended Physical Unclonable Function (PUF) support via an internal PUF, as well as an optional external PUF
Keep on reading: RT-600 Root of Trust Series, A New Generation of Security Anchored in Hardware »
What is Quantum Safe Cryptography?
The RT-600 Root of Trust series is at the forefront of a new category of programmable hardware-based security cores with its new Quantum Safe Cryptography features.
Once sufficiently powerful quantum computers exist, traditional asymmetric cryptographic methods for key exchange and digital signatures will be easily broken. New cryptographic algorithms known as quantum safe cryptography (QSC) or post-quantum cryptography (PQC) are needed to protect against quantum computer attacks.
The latest generation of Rambus Root of Trust IP offers a state-of-the-art programmable security solution to protect hardware and data with NIST and CNSA quantum-resistant algorithms. The Quantum Safe Engine operates with the CRYSTALS-Kyber and CRYSTALS-Dilithium algorithms, as well as the stateful hash-based signature schemes XMSS (eXtended Merkle Signature Scheme) or LMS (Leighton-Micali Signatures).
Keep on reading: Protecting Data and Devices Now and in the Quantum Computing Era »
Is there a Rambus Root of Trust configured for my application?
There are Rambus Root of Trust solutions tailored to address the specific security requirements and certification standards of nearly every application:
- The RT-100 series of Root of Trust solutions are designed for use in power and space-constrained applications as in IoT devices. Featuring a firmware-controlled architecture with dedicated secure memories, the RT-100 hardware Root of Trust cores provides a variety of cryptographic accelerators including AES, SHA-2, RSA and ECC. There are versions which include SM2, SM3 and SM4 accelerators for the China market.
- The RT-630 is a fully programmable, FIPS 140-3 compliant, hardware security core offering security-by-design for data center cloud, AI/ML, as well as general purpose semiconductor applications. It protects against a wide range of hardware and software attacks through state-of-the-art anti-tamper and security techniques. There are versions of the RT-630 tailored to the China (RT-631) and IoT (RT-632) markets, and the RT-634 includes a Quantum Safe Engine.
- The RT-640 and RT-645 are tailored for the automotive market offering ISO-26262 ASIL-B and ASIL-D implementations respectively. These support vehicle-to-vehicle and vehicle-to-infrastructure (V2X), advanced driver-assistance systems (ADAS) and infotainment uses. The RT-641 is ASIL-B compliant and includes the SM2, SM3 and SM4 accelerators for the China market.
- For highly-secure data center and government-focused chip designs, the RT-650 and RT-660 are FIPS 140-3 compliant and offer DPA and FIA protection respectively. There are versions of the RT-650 and RT-660 that include a Quantum Safe Engine.
- CryptoCell and CryptoIsland Root of Trust solutions are programmable, FIPS 140-3 certifiable hardware security modules. They are designed to be integrated into Arm TrustZone-based SoCs or FPGAs where power and space are a consideration.
Find out more: See all Rambus Root of Trust IP Solutions »
What should I keep in mind when selecting a Root of Trust IP?
Root of Trust product designs vary greatly in architecture and capabilities. When selecting a Root of Trust solution, it’s important to ask the right questions to ensure the best level of protection for your specific security needs.
-
- Some questions to consider include:
- What is the end use of the chip?
- Who and what are you protecting against?
- What is the risk of a compromised device?
- What certifications are required?
It’s also worth noting that Root of Trust products can be tailored to match an applications security threat model, use case, industry segment, lifetime, cost, and geography. Some examples of the different criteria that can be selected include the crypto algorithms, security/anti-tamper mechanisms, and provisioning methods used.
Explore more primers:
– Compute Express link: All you need to know
– PCI Express 5 vs. 4: What’s New?
– Side-channel attacks: explained
– DDR5 vs DDR4 – All the Design Challenges & Advantages
– MACsec Explained: From A to Z
– The Ultimate Guide to HBM2E Implementation & Selection

Leave a Reply