3GPP Kasumi family of accelerators.
Kasumi-IP-06 3GPP Kasumi Accelerators
Home > Security IP > Crypto Accelerator Cores > Kasumi-IP-06
The Kasumi-IP-06 (EIP-06) cipher accelerators implement the specification of the 3GPP Confidentiality and Integrity Algorithms as specified in 3GPP TS 35.201 and 3GPP TS 35.202. Designed for fast integration, low gate count and full transforms, the Kasumi-06 accelerator provides a reliable and cost-effective embedded IP solution that is easy to integrate into high speed SoCs for base stations or other equipment requiring 3GPP support.
Available in two configurations / performance grades.
Targeting Base Station designs.
How the Kasumi-IP-06 3GPP Kasumi Accelerators work
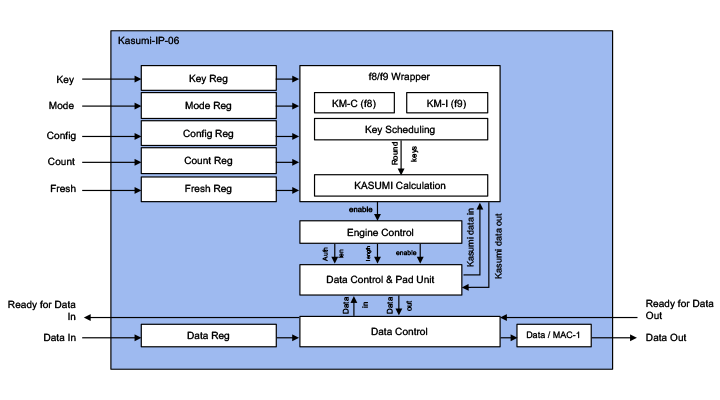
The Kasumi-IP-06 is a family of the cryptographic library elements in the Rambus hardware IP library (formerly of Inside Secure). For example, the Kasumi-IP-06 is the cipher core embedded in some PacketEngine-IP-97/196/197 protocol-aware security engines. The accelerators include I/O registers, encryption and decryption cores, and the logic for feedback modes and key scheduling.
Sustained performance for any object sizes ranges from 2.4 to 5 Gbps depending on the configuration, area and frequency. Gate count is around 20K gates depending on the configuration. Supported modes: UEA2, UIA2, f8. F9.
Rambus also offers accelerators for the other 3GPP algorithms.

Anti-Tampering Technologies
The design of chip anti-tamper protection needs to adapt and scale with rising threats. Adversaries range from high school hackers to well-funded state actors. Given the threats, it’s useful to think about anti-tamper countermeasures as a hierarchy of safeguards that parallel the type, effort and expense of attacks. Watch this webinar to learn the eleven kinds of tampering attacks and their required skills and resources, and countermeasures for each of these attacks.
Kasumi-IP-06 Information
Key benefits:
- Silicon-proven implementation
- Fast and easy to integrate into SoCs
- Flexible layered design.
- Complete range of configurations
- World-class technical support
Features:
- Wide bus interface (64-bit data, 128-bit keys) or 32-bit register interface.
- Includes key scheduling hardware.
- Modes Kasumi
- Algorithms f8 and f9.
- Fully synchronous design.
- Low Speed, High Speed versions.

Introduction to Side-Channel Attacks
Side-channel attacks conducted against electronic gear are relatively simple and inexpensive to execute. Such attacks include simple power analysis (SPA) and Differential Power Analysis (DPA). As all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.



