CryptoManager Provisioning
Home > Security IP > Provisioning and Key Management > CryptoManager Provisioning
The Rambus CryptoManager Provisioning is a secure supply chain solution for semiconductor and device manufacturers, enabling insertion of keys and other secure data. Designed to seamlessly integrate into existing manufacturing flows with minimal interruption, CryptoManager Provisioning currently secures over 2 billion devices per year (and counting).
How CryptoManager Provisioning works
CryptoManager Provisioning enables the secure insertion of cryptographic keys and other sensitive data throughout a distributed supply chain, including both captive and 3rd party (untrusted) manufacturing locations. CryptoManager Provisioning capabilities cover a broad range of secure operations, including key delivery and programming, protection of debug and other sensitive ports, and feature configuration for chips and devices. It supports provisioning of device-specific information to any on-chip secure enclave, including the Rambus family of CryptoManager Root of Trust cores.
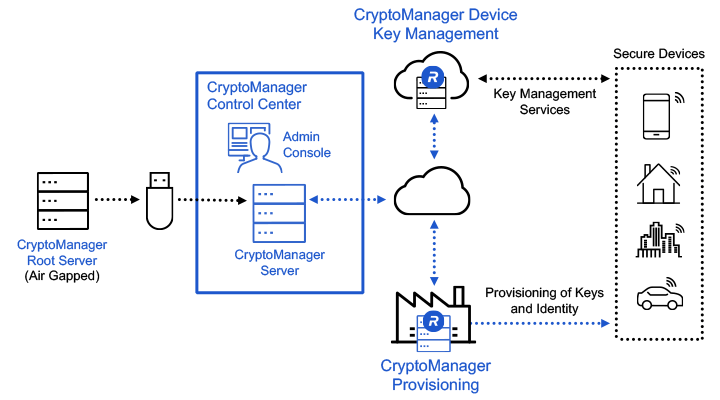
Security starts in the CryptoManager Control Center. It enables simple and intuitive administration for secure provisioning of high value keys and data into semiconductor devices. Removing the human element out of key injection, secret cryptographic keys are protected end-to-end and injected automatically, enabling manufacturing integrity and security. As the keys are only known to the semiconductor OEM (and not others), they can be guaranteed secure. These cryptographic keys are the foundation of device security: device authentication, attestation, and unique identification.
CryptoManager Provisioning works in conjunction with CryptoManager Device Key Management to provide an end-to-end security solution for chips and devices. CryptoManager Device Key Management is a cloud-based software platform that enables customers to build and deploy key management services that leverage hardware-provisioned keys and certificates in semiconductors and devices over the entire device lifecycle.
CryptoManager Provisioning is a foundational product in any secure supply chain ecosystem.
Solution Offerings
- Cluster support for high availability and scalability
- Dynamic SKU management
- Ability to provision secure data to any secure IP core or chipset
- Comprehensive system monitors and alerts
- Secure browser-based management console
- Business continuity/disaster recovery
- Meets manufacturing critical performance requirements
- Advanced key and data management
- Verify manufacturing volumes, yields, and configurations
- Monitor production status, availability, and inventory levels
- Protect against cloning, reverse engineering, counterfeiting, and overbuilding
- Secure offline Root Authority for managing system permissions and authorizations
- Provision cryptographic information securely in untrusted environments
- Advanced encrypted key and data storage
- Two-factor user authentication
CryptoManager Provisioning Equipment
- Root Authority (optional)
- Server (Cluster)
- Appliance (Cluster)
CryptoManager Control Center
Full Documentation
- Root Authority Guide
- Service Guide
- Appliance Guide
- Admin Console API Guide
Support
- 24×7 Infrastructure Support
- Software Maintenance
| CryptoManager Control Center | The CryptoManager Control Center is a security control system that works in conjunction with an off-line Root Authority. It manages the distribution of data assets with the appropriate authorizations to connected CryptoManager Appliances. It includes an easy-to-use Administration Console for operators to centrally manage the Infrastructure across multiple manufacturing sites. |
| CryptoManager Appliance | The Appliance is a tamper-resistant, rack-mounted server, deployed in high-volume manufacturing facilities or cloud services data centers, that provides local security and handles the distribution and programming of secret keys and device configuration data. It also delivers secure production logs and system health data to the Control Center. The appliance is designed to integrate with existing test equipment. |
Protecting Safety, Revenue and Brand: Combating Counterfeit Semiconductors in the Automotive Supply Chain
The counterfeit market for semiconductors is real, sizable and growing. Industry analysts peg the current market for fake semiconductors at $75B. Counterfeit chips pose great risk to driver comfort and safety, to say nothing of the severe negative consequences they present to automaker revenues and brand. The good news is there are immediate and cost-effective measures available to secure the semiconductor supply chain and stop counterfeiters in their tracks.Use Cases
Personalization
Large OEM customers requesting personalization, customer specific data preparation and feature customization of standard parts challenge the chipmakers ability to minimize inventory overhead and improve operating efficiencies.
Secure Key Provisioning
With mobile devices housing more and more sensitive data that is utilized in a wide variety of applications, chip and device companies must meet the complex security requirements for each potential use case or capability.Debug Access Control
The CryptoManager solution provides a method for chip and device companies to authenticate the device and authorize the provisioning of the debug enable/disable operation for each device.
Resources
Videos