Home > Security IP > Protocol Engines > High Speed Public Key Accelerator
Security
High Speed Public Key Accelerator
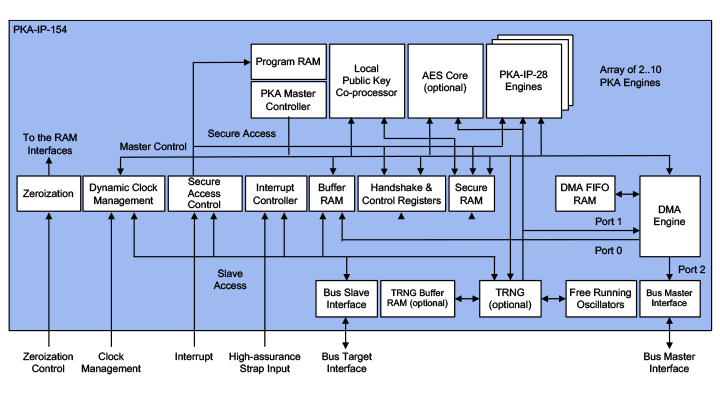
The Rambus High Speed Public Key Accelerator PKI-IP-154 (EIP-154 formerly the Inside Secure) is a family of cryptographic IP cores designed for full scalability and an optimal performance over gate count ratio. The PKA-IP-154 can be deployed in any semiconductor design that needs key exchange or key generation at extreme high performance. The PKI-IP-154 public key accelerators combine an array of Public Key Accelerators (PKA) from the Rambus PKA-IP-28 and True Random Number Generators (TRNG) from the Rambus TRNG-IP-76 with an AMBA interface such as AXI or AHB.
Up to 4160-bit modulus size for RSA & 768-bit modulus for prime field ECC operations.
Two different performance configurations for RSA/CRT operations
Extreme performance public key signature generation, verification & key negotiation.
How the High Speed Public Key Accelerator works
The PKI-IP-154 public key accelerators are suitable for a wide range of applications:
- High performance (Elliptic Curve) Diffie-Hellman key negotiation engines for secure router boxes, secure network interfaces and SSL servers.
- High performance secure Public Key signature generator/checker engines in Hardware Security Modules.
The PKI-IP-154 is available in two different performance configurations that have gate counts of 350K and 1000K, each providing the full set of TRNG and PKA operations with up to 4160-bit modulus size for modular exponentiations and 768-bit modulus for prime field ECC operations. The PKI-IP-154 is a security conscious design and can be provided with or without protection against side channel attacks.
Technical Specifications
Performance @500MHz for the 10 engine solution:
- DH 180/1K-bit exp/mod negotiate: 42,250 ops/s
- RSA 1K-bit sign (no CRT): 8,600 ops/s
- RSA 1K-bit sign (with CRT): 22,630 ops/s
- RSA 1K-bit verify (17 bits exp): 103,000 ops/s
- DSA 160/512-bit exp/mod sign: 46,250 ops/s
- DSA 160/512-bit exp/mod verify: 31,880 ops/s
- ECDSA 192-bit sign: 12,500 ops/s
- ECDSA 192-bit verify: 7,630 ops/s
- ECDSA 384-bit sign: 4,130 ops/s
- ECDSA 384-bit verify: 2,310 ops/s
- ECDSA 521-bit sign: 2,310 ops/s
- ECDSA 521-bit verify: 1,190 ops/s
- Runs faster in 28nm (700MHz) and 16nm (800MHz), performance scales with smaller process nodes.