RT-131 Root of Trust
Foundational security in SoCs and FPGAs for Chinese IoT servers, gateways, edge devices and sensors
Home > Security IP > Root of Trust Solutions > RT-131
Designed to be integrated in power and space-constrained SoCs or FPGAs, the RT-131 Root of Trust (formerly VaultIP) is a FIPS 140-3 compliant hardware core that guards the most sensitive assets on chips and establishes the foundation for platform security.
Featuring a firmware-controlled architecture with dedicated secure memories, the RT-131 hardware Root of Trust provides a variety of cryptographic accelerators including AES, SHA-2, OSCCA SM2/SM3/SM4, RSA and ECC. Ideal for power and space-sensitive applications like Chinese IoT server, gateway and edge devices, the RT-131 Root of Trust offers the best balance of size and performance available on the market.
The RT-131 offers a series of key security use cases ‘out of the box’, including:
- Secure Boot assist to host CPU(s) and protection of key material
- Secure firmware upgrade management for Host CPU
- Lifecycle management support
- Secure Debug support
- Secure device authentication and identity protection
The RT-131 provides a secure asset store:
- Only the RT-131 can manage, use and access the assets
- The O/S and applications cannot access key values
- Applications request asset use by reference
- Enforces policies for access and use of keys and cryptographic functions
- Key generation, derivation, storage and transport

Security in the ARM Ecosystem
Building security in an SoC aiming to meet the goals set by the ARM Platform Security Architecture (PSA) is a complex matter. This is compounded by the complexity of modern-day SoCs comprising multiple processors, security domains and security levels. The Rambus root of trust provides a solid foundation for the SoC security architecture ticking ‘all the boxes’ for reaching the security goals, while offering extensive support for effective integration into a complex TrustZone-based SoC infrastructure.How the Root of Trust Works
The RT-131 Root of Trust is a silicon IP core developed to protect an SoC platform and its operation. It allows the SoC to boot securely and protects sensitive key material and assets. At its heart, its Secure Asset Store secretly generates keys and securely stores them. Fully featured, its cryptographic data plane associated to its DMA offloads the main CPU while never exposing secret data to the OS or the applications. It is designed to provide secure, energy efficient and accelerated security functions.
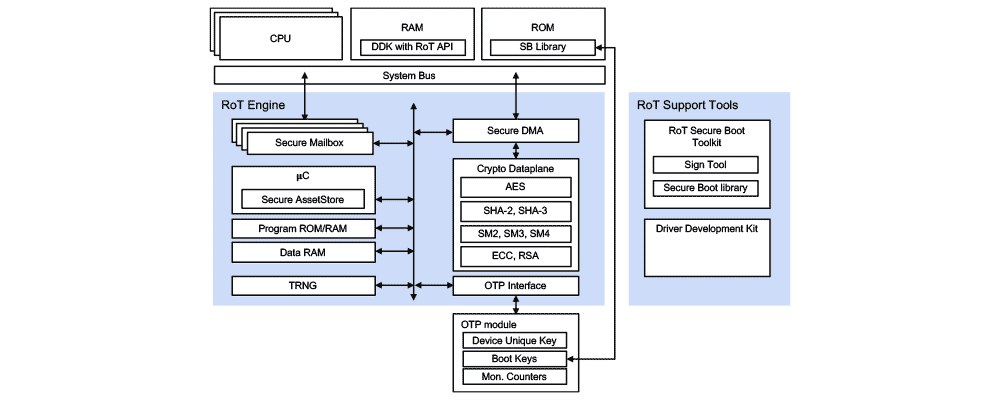
Readily deployable, the RT-131 Root of Trust is offered in off-the-shelf configurations, allowing a choice tailored to the needs of your application. Configurations differ by cryptographic accelerators contained and 3rd-party certification and standard compliance.
The RT-131 is part of the broad Rambus Root of Trust portfolio, which ranges from small, lightweight cores designed to protect IoT endpoints all the way to fully programmable Root of Trust cores designed to protect the most sensitive government/defense chips and automotive deployments requiring ISO-26262 certifications.
Rambus can optionally offer dedicated FIPS 140-3 support packages to its licensees that provide FIPS 140-3 related certification documentation, FIPS test scripts, and dedicated FIPS support.

The Road to Post Quantum Cryptography
Quantum computing offers the promise of tremendous leaps in processing power over current digital computers. But for the public-key cryptography algorithms used today for e-commerce, mobile payments, media streaming, digital signatures and more, quantum computing represents an existential event. Quantum computers may be able to break the widely used RSA and ECC (Elliptic-Curve Cryptography) algorithms in as little as days. Learn about our solutions and recommendations to ready customers for a post-quantum world.
Solution Offerings
| Feature | Description | Details |
| FIPS 140-3 | CAVP and CMVP Compliant | Includes CAVP certificates for NIST approved algorithms and TRNG |
| Cipher Algorithm Support | AES (all key sizes) SM4 (128-bit key) Optional: ChaCha20, ARIA | Modes: CBC, CTR, CCM, CMAC, GCM, XTS Modes: CBC, CTR, GCM ARIA Modes: CBC, CTR, CMAC, CCM, GCM |
| Hash Algorithms | SHA-1, SHA-2 SM3 Optional: SHA-3 | SHA-2 224-256-384-512 SHA-3 224-256-384-512 |
| Message Authentication Code Algorithms | HMAC-SHA-1, HMAC-SHA-2, HMAC-SM3 Optional: HMAC-SHA3 | SHA-2 224-256-384-512 SHA-3 224-256-384-512 |
| AEAD Algorithms | AES-GCM, AES-GMAC, AES-CCM Optional: ChaCha20/Poly1305, ARIA-CCM | Modes: GCM, GMAC, CCM |
| Signature Generation and Verification | ECDSA EdDSA SM2DSA RSA up to 3096 bits | NIST P-224, P-256, P-384, P-521 Ed25519 |
| Key Agreement Algorithms | ECDH DH EdDH | NIST P-224, P-256, P-384, P-521 Up to 3096 bits Curve25519 |
| Key Transport Algorithms | ECIES RSA Wrap/Unwrap (RSA-OAEP) SM2-WRAP AES-WRAP SM4-WRAP | 128- and 256-bit strength Up to 3096 bits128- and 256-bit strength 128-bit strength |
| True Random Number Generator | NIST SP800-90A/B/C | NIST ENT certificate |
| Crypto Performance | Cipher/Hash Performance (Gbps) @500MHz | Scalable, ~2 Gbps |
| I/O Bus | AMBA Bus Master/Slave | AXI/AHB Master, AXI/AHB/APB Slave |
| OTP Interface | Interface to 3rd-Party OTP | TCM |
- Cloud-connected devices
- IoT (Internet of Things) devices
- Industrial IoT
- Sensors
- Gateways
Full Disk Encryption of Solid State Drives and Root of Trust
File encryption, file system encryption and full disk encryption (FDE) are methods offered by the industry to allow users to protect their data stored on non-volatile storage devices, such as Solid State Disks (SSD). The main feature of FDE is to protect stored system and user date from unauthorized reading, writing, alteration, moving or rolling back. However, extended security features are key to securing FDE implementation.