Home > Security IP > Root of Trust Solutions > CryptoManager RT-6xx Root of Trust Family
The CryptoManager RT-6xx v3 Root of Trust family from Rambus is the latest generation of fully programmable FIPS 140-3 compliant hardware security cores offering Quantum Safe security by design for data center and other highly secure applications.
Device and system architects face a growing array of security threats, including the threat of quantum computers. Across applications, one constant is the need for a hardware Root of Trust-based security implementation.
The CryptoManager RT-6xx family protects against a wide range of hardware and software attacks through state-of-the-art side channel attack countermeasures and anti-tamper and security techniques. The RT-6xx supports various security certifications up to level 3. The RT-6×4 Root of Trust adds Quantum Safe Encryption (QSE) to provide a future-proof hardware security solution to protect data center assets starting today and into the quantum era.
The RT-6xx allows customers to develop secure and trusted applications that run securely within a trusted boundary. Secure applications can be assigned unique roots and keys, allowing independent permissions and access levels.
CryptoManager RT-6xx Root of Trust Family: A New Generation of Security Anchored in Hardware

This latest generation CryptoManager RT-6xx Root of Trust IP offers many new features designed to support the security needs of customers today and in the future. These features include Quantum Safe Cryptography, Caliptra Root of Trust for Measurement (RoTM) emulation, DPA and FIA protections, as well as an innovative three-tier architecture that lets customers tailor a Root of Trust solution to their specific requirements.
How the CryptoManager RT-6xx Root of Trust Works
The CryptoManager RT-6xx Root of Trust is a siloed hardware security IP core for integration into semiconductors, offering secure execution of authenticated user applications, tamper detection and protection, secure storage and handling of keys and security assets, and optional resistance to side-channel attacks. The Root of Trust is easily integrated with industry-standard interfaces and system architectures and includes standard hardware cryptographic cores. Access to crypto modules, keys, memory ranges, I/O, and other resources is enforced in hardware. Critical operations, including key derivation and storage, are performed in hardware with no access by software. The Root of Trust is based on a custom 32-bit processor designed specifically to provide a trusted foundation for secure processing on chip and in the system. The RT-6xx inherits its flexible cryptographic accelerator from the embedded Rambus CryptoManager Hub CH-6xx cores.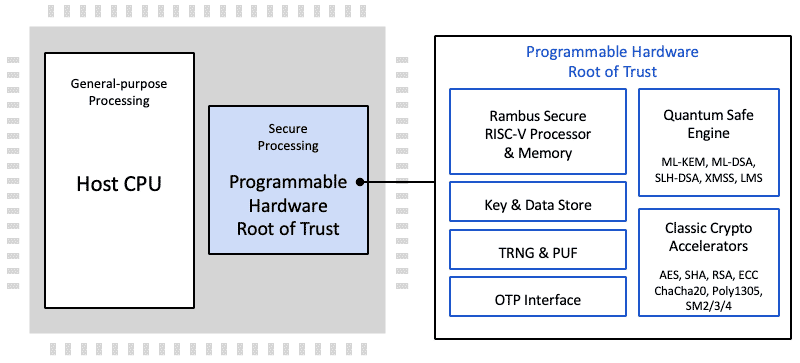
The Root of Trust supports all common host processor architectures including ARM, RISC-V, x86 and others. The multi-threaded secure processor runs customer developed signed code either as a monolithic supervisor or as loadable security applications which include permissions and security-related metadata. It can implement standard security functionality provided by Rambus, or complete customer-specific security applications, including key and data provisioning, security protocols, biometric applications, secure boot, secure firmware update, and many more.
Protecting Data and Devices Now and in the Quantum Computing Era

Quantum computing is being pursued across industry, government and academia with tremendous energy and is set to become a reality in the not-so-distant future. Once sufficiently large quantum computers exist, traditional asymmetric cryptographic methods for key exchange and digital signatures will be broken. Many initiatives have been launched throughout the world to develop and deploy new quantum-resistant cryptographic algorithms, known as Post-Quantum Cryptography (PQC).
Solution Offerings
- Custom-designed, customer programmable 32-bit secure RISC-V processor
- AXI Interface to SoC, and fast 64-bit addressable DMA to host memory
- Multi-layered security model protecting all core components against a wide range of attacks. The security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- Secure data store allowing assets generated during boot available for secure applications
- Wide range of classic and Quantum Safe cryptographic accelerators and security modules, such as canary logic for protection against glitching and overclocking, secure key derivation
- State-of-the-art anti-tamper mechanisms against DPA and FIA side channel attacks
Cryptographic Accelerators by Product
| Product | Cryptographic Accelerators Supported |
|---|---|
| RT-630 | NIST CMVP compliant. NIST CAVP hardware cryptographic accelerators including AES (all modes), HMAC, SHA-2/3 (all modes), RSA up to 4096 or 8192 bits, ECC up to 521 bits, a NIST SP 800-90A/B certified TRNG. LMS and XMSS hash-based signature schemes and SHAKE XOF boot flow |
| RT-660 | As per RT-630 + DPA-resistant and FIA-protected cryptographic accelerators |
| RT-631/RT-661 | As per RT-630/RT-660 + Chinese Encryption with OSCCA SM2/3/4 |
| RT-634/RT-664 | As per RT-630/RT-660 + CNSA Quantum Safe Cryptography (ML-KEM, ML-DSA, SLH-DSA) and boot flow |
| RT-635 | As per RT-631 + CNSA Quantum Safe Cryptography (ML-KEM, ML-DSA, SLH-DSA) and boot flow |
| RT-639/RT-669 | As per RT-634/RT-664 + Caliptra Root of Trust for Measurement with Dice and X.509 support (1.1/2.0) |
Complete Documentation
- Integration guides
- Reference manuals
- Programming guides
- Optional FIPS 140-3 support package
RTL and FW Package
- Verilog RTL for synthesis and simulation
- Standard EDA tool flow scripts and support files
- Verification test bench and test vectors
- Boot loaders and secure RTOS and security monitor firmware
- HLOS APIs for accessing RT-6xx capabilities
SW SDK Package
- SDK including the development environment, complete emulation with debugging capabilities of the RISC-V and crypto cores on QEMU
- One-step install emulation with multiple samples and reference code to help customers kickstart their secure application development