Trend Micro has confirmed a 752% increase in ransomware families during 2016, with spam ranked the top infection vector. According to the cyber security company, the availability of open source ransomware and ransomware-as-a-service (RaaS) will continue to make it easier for cyber criminals to run their own ransomware operations.
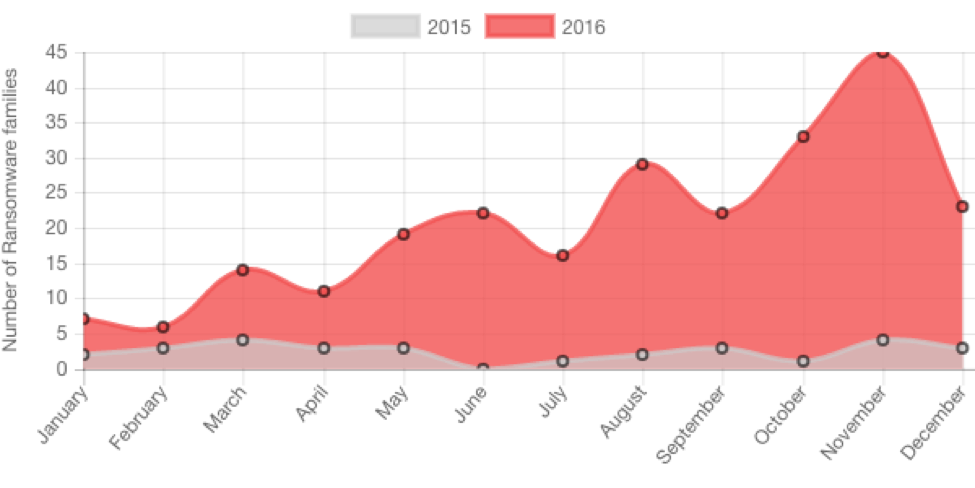
Image Credit: Trend Micro
“Organizations should therefore stay vigilant to avoid losing data and money and experiencing significant system downtime,” Trend Micro researchers recommended.
As ZDNet’s Danny Palmer notes, it takes only seconds for ransomware to block access to an entire network. Nevertheless, most businesses remain locked out of crucial files and systems for a week or more, with the impact causing severe financial and reputational damage.
“Data gathered [by Timico and Datto] from over a thousand businesses which have been victims of ransomware within the last year suggests that 85 percent of those infected by the malicious file encrypting software had their systems forced offline for at least a week, while a third of cases resulted in data being inaccessible for a month or more,” he explained. “Worryingly, 15 percent of those targeted with ransomware found that their data was completely unrecoverable.”
According to Asaf Ashkenazi, senior director of Product Marketing at Rambus, ransomware has become everyone’s problem.

“To cyber criminals, nearly every device is a potentially lucrative target – not just critical infrastructure like an electric company, or big businesses, universities, public transportation systems and hospitals,” he explained in a recent Seminconductor Engineering article. “Therefore, implementing an effective security solution must be a priority, even for mid-size and small businesses.”
As Ashkenazi emphasizes, security solutions should be ready out of the box: simple, affordable and easy to use.
“This is even more [critical] for IoT devices and their cloud services,” he continued. “One way of simplifying security and reducing costs is using IoT devices with a tamper-proof pre-provisioning key and identifier, which enable out-of-the-box secure connectivity and other security features. That allows service providers to bolster security for a wide range of connected ’things.’”
Ashkenazi also points out that mass adoption of ‘plug and play’ security solutions by IoT OEMs and IoT platform providers will allow small and medium businesses to easily and affordably adopt security, which will hopefully act as a positive catalyst to change the current status quo when it comes to unchecked ransomware activities by cyber criminals.
“Minimizing the number of unprotected endpoints can help reduce the success rate of ransomware, hopefully discouraging cyber criminals from participating in an increasingly unprofitable business,” he concluded.
