In a recently published paper, security researchers built a miniature system capable of covertly recovering encryption keys using side-channel analysis. Fox-IT’s Craig Ramsay and Jasper Lohuis collaborated with Riscure to perform this analysis against two realistic AES-256 implementations. Specifically, the attacks were conducted using an improved antenna and signal processing equipment that cost less than €200 and fit into a jacket pocket. Moreover, the entire operation spanned five minutes at a distance of one meter, dropping down to a quick 50 seconds for 30 cm.
Have you read our primer?
– Side-channel attacks: explained
“Some things are just inherent to electronic products. TEMPEST leakage is one of them. This holds true for any appliance — whether programmed in JavaScript, C, or even a custom hardware design. Everything is eventually run on hardware (a.k.a. electronics),” Ramsay and Lohuis explained. “So, running an algorithm will produce some fluctuating magnetic field. There is often nothing preventing us from measuring this EM radiation from close by, or even covertly from a distance. In fact, this is a technique which is relied upon in all wireless communication. All FM radio, WiFi, and GSM communications work by deliberately exploiting this. TEMPEST attacks measure this field from a distance and extract useful information from it.”
For the attack executed at 30 cm, Fox-IT targeted the ARM Cortex-M3 core powering the SmartFusion2 SoC. Security researchers used a small magnetic loop antenna, an external amplifier and bandpass filters, as well as a €20 USB RTL-SDR USB dongle for data recording. (The researchers also worked with SR-7100 and USRP B200 data recorders). Preprocessing, first extracted one large recording from the radio, then detected where each encryption block started and split the recording up into single encryption blocks. Subsequent analysis was performed by correlating between key byte guesses and the recorded traces to retrieve the secret key.
“[On the] SmartFusion2 target, the leakage seems to largely originate from the AHB bus connecting the Cortex-M3 to the on-chip memories. We can correlate on the addresses of the T table lookups to attack the key,” Ramsay and Lohuis explained. “We count the number of bits which transition between two sequential addresses on the bus (i.e. Hamming distance). This suggests that the bus logic briefly short-circuits when transitioning.”
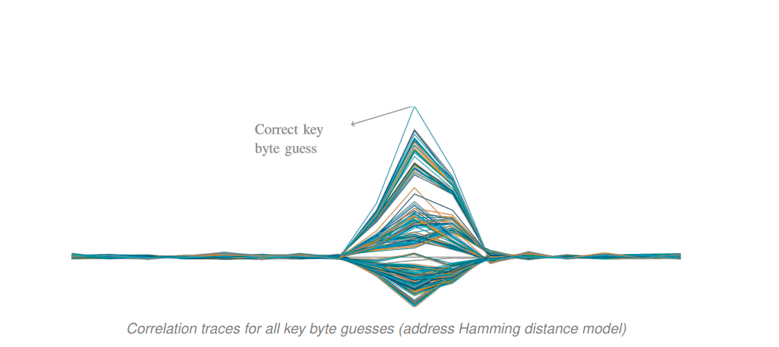
Image Credit: Fox-IT
The plot above shows the correlation traces for all 256 guesses of a key byte using the Fox-IT address line model. As the image illustrates, the correct byte does indeed provide the highest spike, meaning the key (byte by byte) can be recovered using only measurements and the input data.
To perform the TEMPEST attack at a distance, security researchers switched to a more directional PCB log-periodic antenna that targeted a Pynq board.
“The software is still the same, we still attack the bus between ARM core and memory, but we can clock the memory at 400 MHz,” Ramsay and Lohuis continued. “We find switching to the new board surprising easy. Although the memory clock is ≈3 times faster (or effectively ≈6 as we now use DDR), we can still attack the Pynq board with the bandwidth supported by the RTL-SDR.”
For the next stage of the TEMPEST side-channel attack project, the researchers built a shielded chamber to reduce the effect of external signals using two boxes wrapped with emergency blankets – later moving their equipment to an anechoic chamber at OSPL, an environment essentially free of external signals and most reflections of internal signals.
“We use a discone antenna (also seen below) to measure omnidirectionally with a very wide frequency range,” Ramsay and Lohuis concluded. “Even with our <€200 (excluding antenna) recording setup we are able to successfully attack the Pynq board from 1 m distance. This is possible with 5 minutes of recording time which captures ≈2.4 million traces. This result shows that, under ideal conditions, attacks from 1 m are definitely possible.”
It should be noted that Rambus’ security division originally discovered and published side-channel analysis in the 1990s and has also demonstrated side-channel attacks in recent years. EM side-channel work by Rambus’ security division include analysis of mobile phones and analysis of a complex system-on-chip.

