In the late 19th century, Dutch cryptographer Auguste Kerckhoff postulated what has become known as “Kerckhoff’s Principle” — a cryptosystem should be secure even if everything about the system, except the key, is public knowledge.
Since Kerckhoff’s days, cryptography has certainly evolved. A modern interpretation of Kerckhoff teaches that you shouldn’t rely on the obscurity of your crypto algorithm, but rely instead on standard algorithms with strong key sizes. A natural assumption might be that standard algorithms would be able to conceal themselves, making it difficult to determine the algorithm in use. This actually isn’t the case – and isn’t even necessary for a security sub-system to resist attacks. Suppose you’re using a NIST-standard algorithm in your device — how is anyone ever going to know? Can an adversary tell what algorithm you’re using? It turns out they can – but that’s ok.
Using inexpensive tools, electromagnetic and/or power data from a semiconductor can be captured. That data can used to determine what cryptographic algorithm is being deployed; experienced analysts are often able to readily identify the algorithm deployed simply by looking at a series of waveforms. For instance, a waveform with 10 distinct rounds may indicate a 128-bit AES encryption standard (shown in Figure 1), whereas a 14 round waveform may indicate a 256-bit AES. Other popular cryptographic algorithms like RSA (shown in Figure 2), SHA, and Elliptic Curve all have a distinct “signatures” which may inform the analyses (i.e. the adversary) what algorithm is being executed, the key size, and where it’s happening in the overall computational process.
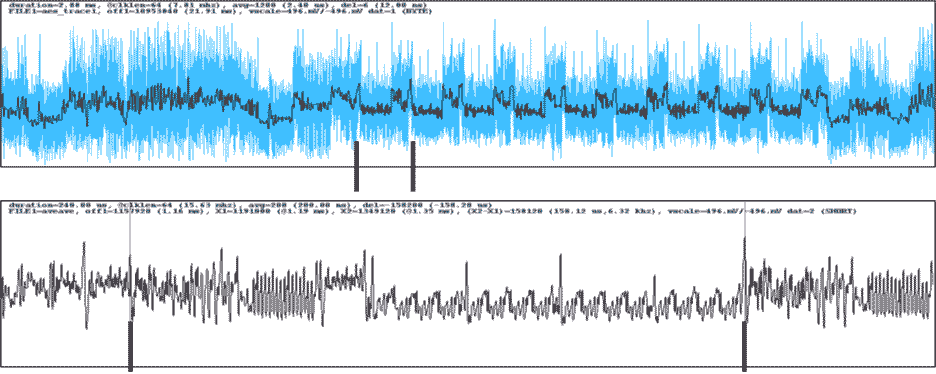
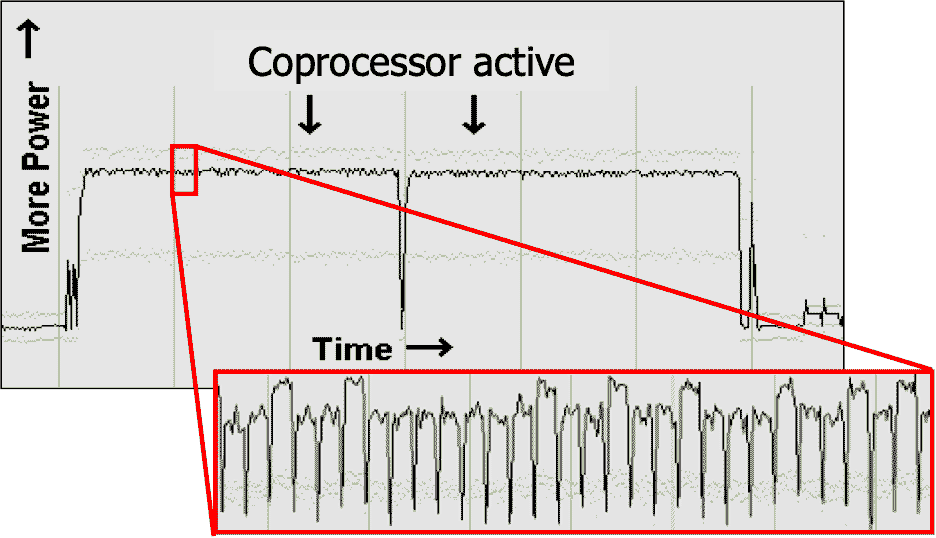
So why Is knowledge of the algorithm deployed not a concern? This is the heart of Kerckhoff’s teachings. All NIST-standard algorithms derive security from the secrecy of the key and the cryptographic strength of the algorithm, but not the secrecy of the algorithm. And that secret key value is completely independent of the algorithm deployed – while the algorithm requires a certain size of key (e.g., AES-256 requires a 256-bit key value), the value of the key can be random set of digits. A 128-bit key has 2128 possible key combinations: that’s 340,282,366,920,938,463,463,374,607,431,768,211,456 combinations, which is 39 digits long – not something easily guessed! Without knowing the secret key value, adversaries have no way to penetrate the security of the chip, even if they have perfect knowledge of the algorithms deployed within the chip. The attack vector thus shifts to extracting the key, not what cryptographic algorithm(s) the device is running.
There are a multitude of attack vectors that adversaries use to extract the secret key which are known as Side-Channel Attacks, which include Differential Power Analysis (DPA), Simple Power Analysis (SPA), Simple Electromagnetic Analysis (SEMA), Differential Electromagnetic Analysis (DEMA), Correlation Power Analysis (CPA) and Correlation Electromagnetic Analysis (CEMA). Side-channel attacks work on the reality that all physical electronic systems routinely leak information about the internal process of computing via fluctuating levels of power consumption and electromagnetic emissions. Rather than using brute force attacks, side-channel attacks exploit those leaks by repeatedly capturing and analyzing samples. Rambus’s Differential Power Analysis Workstation is a powerful tool in understanding a device’s resistance to attack.
Perhaps most concerning about side-channel attacks is that while they formerly may have taken a prohibitively expensive level of equipment and expertise, today these attacks can be executed relatively cheaply and easily using off-the-shelf equipment. To combat side-channel attacks, Rambus offers a series of side-channel resistant cryptographic algorithms. Through various techniques, including leakage reduction, noise introduction, obfuscation, and the incorporation of randomness, the protected algorithms are effective at resisting side-channel attacks up to and beyond 1 billion operations, securing our customers’ devices against attack.
Within the industry, we say that “security by obscurity” is a bad idea. While we don’t necessarily recommend publishing your security architecture on the front page of the New York Times, we believe that your architecture should be able to withstand attacks based on that amount of disclosure. Corporate espionage, accidents, vandalism, or even reverse engineering can reveal the design of security. Accepted security best practices don’t involve hiding what security you are deploying, but rather spending your time and efforts on making sure your security is deployed in such a manner that when your security architecture is determined (and it will be!), it is as resistant to as many attacks as possible, just as Kerckhoff spoke of almost 150 years ago.

Leave a Reply