Home > Security IP > DPA Countermeasures > SCA Resistant Cores with DPA and FIA > Anti-Tamper Cryptographic Cores
Security
Anti-Tamper Cryptographic Cores
Rambus DPA (Differential Power Analysis) Resistant Cryptographic hardware cores guard against the various side channel attacks that exploit unprotected cryptographic designs. Easily integrated into an ASIC or FPGA design, these cores resist tampering attacks attempting to obtain secret cryptographic key material through Differential Power Analysis (DPA), Differential Electromagnetic Analysis (DEMA) or Fault Injection Attacks (FIA).
These cores provide robust anti-tamper resistance across different security and performance levels making them ideal for government and defense applications where attack vectors include side channel attacks like DPA, DEMA and FIA.
How the Anti-Tamper Cores Work
The DPA Resistant Hardware Cores offer military and government chip and security architects an easy-to-integrate, technology-independent soft-macro security solution with built-in DPA, DEMA, Correlation Template Attack (CPA, CEMA) and FIA resistance for cryptographic functions across a wide array of devices.
Rambus DPA Resistant Cores implement DPA countermeasures such as LUT-Masked Dual-rail with Pre-charge Logic (LMDPL) gate level masking and Domain Oriented Model (DOM). DPA and DEMA resistant implementations are available for AES, 3DES, HMAC-SHA-2 and PKE (Public Key Engine implementing RSA and ECC algorithms) accelerators.
In addition, the DPA Resistant Cores protect against CPA and CEMA where an attacker has full access to blank, unprovisioned and unprogrammed devices. In such a case, an attacker can profile the power and electromagnetic behavior of the device and create a template. Using such a template allows for easier CPA or CEMA-based attacks.
These countermeasures are portable to all modern FPGA or ASIC technologies, allowing reuse across hardware platforms and programs. They deliver the highest level of security while meeting silicon area, performance and power budget targets.
All implemented DPA and DEMA countermeasures are extensively validated using the Test Vector Leakage Assessment (TVLA) methodology and are validated to the FIPS 140-2 CAVP standard. Additionally, all cores are validated using the Rambus DPA Workstation.
Rambus FIA Resistant Cores implement detection mechanisms that flag bit flips in registers, in finite state machines, on buses and in cryptographic logic. Bit flips may happen unintentionally or may happen as an effect of active FIA techniques, such as light, laser, voltage or clock glitching. The effect of a successful FIA action can influence the operation of a cryptographic hardware core. Examples include influencing finite state machines to skip cryptographic rounds or skip encryption completely, allowing keys to be read out, or disabling, or reducing the effectiveness of, DPA countermeasures. FIA countermeasures are extensively validated using state-of-the-art fault injection modeling.
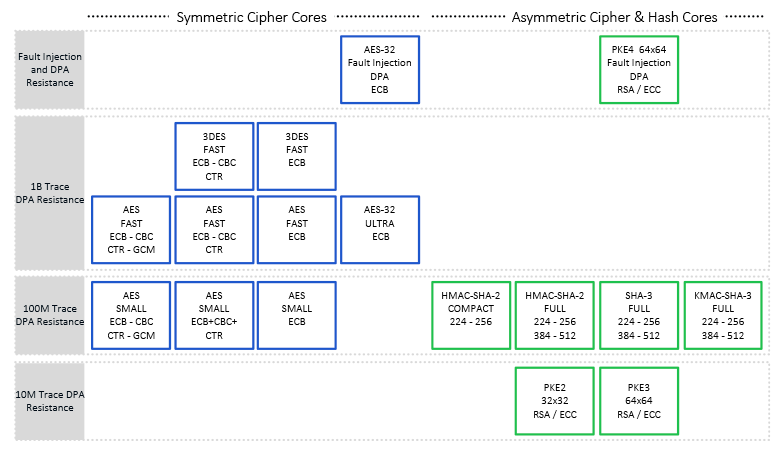
Included in the Side Channel Attack Resistant product family are a series of cores with varying levels of DPA and FIA resistance. DPA and DEMA resistant implementations are available for AES, 3DES, HMAC-SHA-2 and PKE (Public Key Engine implementing RSA and ECC algorithms) accelerators. AES and 3DES resistance extends to 1 billion traces and beyond, HMAC resistance extends up to 100 million traces, and PKE up to 10 million traces.
- CPA and CEMA resistant implementations are available for AES and PKE (Public Key Engine implementing RSA and ECC algorithms) accelerators.
- FIA resistant implementations (including DPA/CPA protection) are available for AES and PKE (Public Key Engine implementing RSA and ECC algorithms) accelerators.
Deep Anti-Tamper Experience
As the inventor and pioneer of DPA and an acknowledged leader in device security, Rambus is uniquely qualified to provide anti-tamper solutions for the most stringent requirements. Rambus technologies protect more than 9 billion chips per year, and as a US-based, independent company, Rambus has the experience and pedigree to be the solution provider of choice. Rambus has for more than 25 years supplied side channel and anti-tamper attack resistant solutions for government and defense applications, including security co-processors, anti-tamper software libraries, and side channel testing workstations.

Introduction to Side-Channel Attacks
Side-channel attacks conducted against electronic gear are relatively simple and inexpensive to execute. Such attacks include simple power analysis (SPA) and Differential Power Analysis (DPA). As all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.