Home > Security IP > Protocol Engines > MACsec Engines > MACsec-IP-165
Security
MACsec-IP-165 / EIP-165 Flow through MACsec for PHY devices, up to 100Gbps
The MACsec-IP-165 (EIP-165) is an IP family for accelerating MACsec up to 100 Gbps, serving single channel PHY designs. The MACsec-IP-165 is a high-performance streaming MACsec frame processing engine that provides hardware acceleration for the complete MACsec frame transform along with frame classification and statistics counter updates. Once the MACsec-IP-165 is configured, no CPU is required for processing tasks.
Protocol aware MACsec Packet Engine with classifier and in-line interface for PHY devices.
1..10..100bps, programmable rules, no CPU required, supports all IEEE MACsec requirements.
Supported by Driver Development Kit, QuickSec MACsec toolkit
How the MACsec-IP-165 works
MACsec is ideally positioned to provide secure WAN (Layer-IP-2) interconnect without the need for routing, allowing networks to be secured from the Inside Secure. The MACsec-IP-165 is designed for being embedded in PHY devices, in between two MAC interfaces. For non PHY designs refer to the MACsec-IP-160 (1..100Gbps) or MACsec-IP-166 (400..600Gbps) cores.
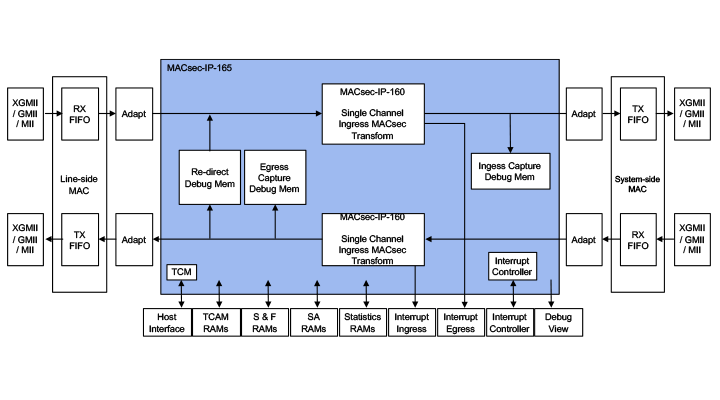
The MACsec-IP-165 is a MACsec engine with integrated VLAN and MACsec packet classification logic and all required statistics counters. The available MACsec-IP-165 configurations cover the applications ranging from 1 Gbps to 100 Gbps. The MACsec-IP-165 is designed to be integrated with two Ethernet MACs to form a plug-in MACsec solution between an existing Ethernet MAC (“system-side”) and an existing Ethernet PHY (“line-side”). A handshaked host bus interface is used to control the MAC-IP-165.
Performance/area (ingress/egress):
- MACsec-IP-165s: 1Gbps FDX @125MHz, 617K gates. 32SAs.
- MACsec-IP-165a: 10Gbps FDX @312.5MHz, 617K gates. 32SAs
- MACsec-IP-165d: 100Gbps FDX @468.75MHz, 3200K gates. 32SAs.
- The gate counts are highly affected by the number of supported SAs. Data is provided for 32SAs, more SAs up to 256 per direction can be supported.
- Frequencies up to 1GHz ASIC and 200MHz FPGA are supported.
MACsec Fundamentals
For end-to-end security of data, it must be secured both when at rest (stored on a connected device) and when in motion (communicated between connected devices). For data at rest, a hardware root of trust anchored in silicon provides that foundation upon which all device security is built. Similarly, MACsec security anchored in hardware at the foundational communication layer (Layer 2) provides that basis of trust for data in motion over Ethernet-based networks.Features & Benefits
Key Benefits:
- Silicon-proven implementation.
- Fast and easy to integrate into SoCs.
- Flexible layered design.
- Complete range of configurations.
- World-class technical support.
- Driver Development Kit.
Classification:
- VLAN and Q-in-Q tag detection.
- MACsec tag detection and sub-classification (absent, valid, invalid and KaY frame).
- MACsec tag after VLAN detection.
- Programmable “control frame” classification.
- 16 to 128 (16 to 256 for EIP-165d)-entry programmable rule lookup with attached operation selection (drop, bypass, MACsec process) and SA information for the MACsec processing.
- 8-entry programmable non-matching flow operation selection (drop, bypass), depending on MACsec tag sub-classification and control frame classification.
- Explicit classification feature, allowing for external selection of the processing flow while ignoring the internal classification.
Latency:
- Cut-through processing support, resulting in a latency that is below 150 ns in both directions, including MACsec transformation, at 468.755 MHz.
- Latency is configurable, allowing constant start-of-frame latency for all types of transformations.
MACsec Processing Features:
- IEEE 802.1AE , 802.1AEbn, IEEE 802.1AEbw compliant.
- All cipher suites supported (GCM-AES-128/256, GCM-AES-XPN-128/256).
- MACsec transform with the VLAN Tag bypassing.
- Statistics counter support (64 bits for frame & octet counters), in saturating or wrapping mode (programmable).
- Programmable confidentiality offset (0..127 Bytes).
- SecTAG insertion and removal.
- ICV checking/removal and calculation/insertion.
- Packet number generation and checking.
- Post-processing controls frame and octet statistics counters at global, SA and VLAN (User Priority) levels.
- Hardware offload for the nextPN and lowestPN update from the host (KaY)
Ingress Path Consistency Checking
- Performed on bypassed and MACsec processed frames.
- 16 to 128 (16 to 256 for EIP-165d)-entry programmable matching table with separate drop/transfer decisions.
- Separate drop/transfer decision for control/non-control frames in case of non-match.
Miscellaneous
- Transparent synchronized transfer of LPidle (IEEE Std. 802.1az) and line/local/remote fault detection signals through the processing engine.
- MTU checking (and optional oversize dropping) dependent on VLAN User Priority level for VLAN frames. Separate check for non-VLAN frames.
- Local interrupt controller to combine internal interrupts into one interrupt output.
- Separate internal interrupt events (if external interrupt controller is used)
- Support for AES-ECB, AES-CTR, AES-GCM/GMAC transformation for FIPS certification of the crypto core.
- A pass-through bus on which data is passed unmodified along with the packet (its width is compile-time configurable).
- An output interface to indicate the number of bytes added/removed from the packet during processing.
Debug Features:
- Debug registers to monitor and test critical logic.
- 40-bit wide debug output bus that can be used to monitor internal buses and states in real-time.
Interfaces
- Line and system side interfaces should connect to an external MAC
- Line-side RX interface (FIFO) – 256-bit wide.
- Line-side TX interface (FIFO) – 256-bit wide.
- System-side RX interface (FIFO) – 256-bit wide.
- System-side TX interface (FIFO) – 256-bit wide.
- 32-bit TCM Host interface.
- Single interrupt output from internal interrupt controller.
- Separate interrupt outputs from ingress and egress MACsec engines.
Verification
- Set of test vectors for chip integration verification.
- Integration test vectors in a human-readable format.
- Python / Verilog based verification environment.
- 100% verification coverage.

Secure Networking Basics: MACsec, IPsec, and SSL/TLS/DTLS
The MACsec, IPsec and SSL/TLS/DTLS protocols are the primary means of securing data in motion (communicated between connected devices). These protocols can be anchored in hardware or implemented in software as part of an end-to-end security architecture. This white paper provides fundamental information on each of these protocols including their interrelationships and use cases.Resources
Videos