Protocol-IP-97 Multi-Protocol Engine, Look-Aside, 5 Gbps
Home > Security IP > Protocol Engines > Protocol-IP-97
Protocol aware IPsec, SSL, TLS, DTLS, 3GPP, MACsec packet engine with Look-Aside interface for multi-core application processors
5 Gbps, programmable, supports new and legacy crypto algorithms, AMBA interface
Supported by Driver development kit, QuickSec IPsec toolkit
How the Protocol-IP-97 Multi-Protocol Engine works
The Multi-Protocol Engine is a protocol-aware packet engine with a Look-Aside bus interface and a packet transform engine. It is used as a bus master in the data plane of the system and processes packets with very little CPU intervention. This engine supports an AMBA (AXI, AHB, TCM) or a PLB SoC bus interface and can be delivered in different configurations to support IPsec, SSL, TLS and DTLS. Compared to the Protocol-IP-93 it offers higher performance, more algorithms, protocol flexibility through token instructions and efficient prefetching of packets to maintain line-rate throughputs for small and large packets. The Protocol-IP -97 performs complete L3 packet transformations and achieves 2 Gbps full-duplex for any packet size at 500 MHz and above.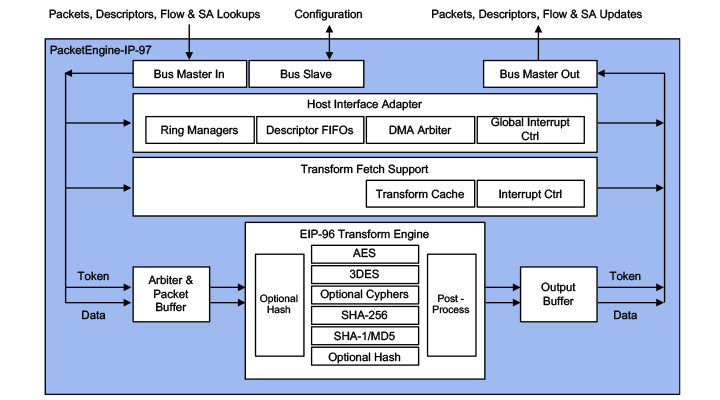
The Multi-Protocol Engine is designed to off-load the host processor to improve the speed of protocol operations and reduce power in gigabit application processors for: VPN routers, home media gateways, FTTH routers, IoT gateways, 5G base stations, edge network equipment, femtocells, VPN appliances and surveillance cameras.
Performance for large packet sizes is well over 5 Gbps for any supported protocol. IPsec performance for small packet sizes is 2.5 Gbps at a clock speed of 500 MHz.

Secure Networking Basics: MACsec, IPsec, and SSL/TLS/DTLS
The MACsec, IPsec and SSL/TLS/DTLS protocols are the primary means of securing data in motion (communicated between connected devices). These protocols can be anchored in hardware or implemented in software as part of an end-to-end security architecture. This white paper provides fundamental information on each of these protocols including their interrelationships and use cases.Features and Benefits
Key benefits:
- Silicon-proven implementation
- Fast and easy to integrate into SoCs
- Flexible layered design
- Complete range of configurations
- World-class technical support
- Descriptor ring infrastructure, with master DMA controller, including Descriptor, SA and packet prefetching
- SA manager
- NIST SP800-90A compliant DRGB
Driver Development Kit.IPsec (IPv4 and IPv6):
- Full IPsec packet ESP/AH transforms according to latest RFCs (2403, 2404, 2405, 2410, 3566, 3602, 3686, 4106, 4301, 4303, 4304, 4308, 4309, 4543, 4835, 4868, 4869, 6054, 6379, 7321, 7539, 7634 and 8221)
- IPsec ESP and AH tunnel & transport mode
- Insert ESP/AH header for outbound packets, strip and verify ESP/AH header for inbound packets
- Full sequence number processing, including ESN and full anti-replay check with various mask sizes
- Calculate and insert Integrity Check Value for outbound packets, strip and verify for inbound packets
- Append (outbound) / strip and verify (inbound) padding up to 255 bytes
SSL3.0 / TLS1.0 / TSL1.1 / TLS1.2 / TLS1.3 / DTLS1.0 / DTLS1.2:
- Full single pass packet transforms according to latest RFCs (246, 4346, 4347, 5246, 5288, 5289, 6101, 6347, 6460, 6655, 7539, 7905 and 8446).
- Full Header processing:
- Insert header for outbound packets,
- Strip and verify header for inbound packets,
- Anti-replay check.
- Trailer processing:
- Insert padding up to 255 bytes for outbound packets,
- Strip and verify padding up to 255 bytes for inbound packets,
- Calculate and insert Message Authentication Code for outbound packets, strip and verify for inbound packets.
MACsec
- MACsec frame transforms according to IEEE 802.1AE
- SecTAG insertion and removal
- PN insertion, removal and verification
- ICV generation, insertion, removal and verification
3GPP Wireless Algorithms
The cryptographic engine supports the following cryptographic algorithms:
- (3)DES in ECB and CBC with (3x) 56-bit key
- AES in ECB, CBC, ICM, CTR mode with 128/192/256 bit keys, GCM, GMAC and CCM modes, optional AES-XTS
- Optional ChaCha20, SM4, ARIA [bullet inserted]
- Optional ARC4 in Stateful and Stateless mode, up to 128-bit key
- Kasumi in basic and f8 mode (UEA1)
- SNOW3G in basic and 128-EEA1 mode (UEA2)
- ZUC in basic and 128-EEA3 mode (UEA3)
The Hash engine supports the following algorithms:
- SHA-1, SHA-2-224/256, MD5
- Optional SHA-2-384/512, SHA-3 224/256/384/512 [bullet inserted]
- HMAC transforms for SHA-1, SHA-2, MD5
- Optional SM3, Poly1305[bullet inserted]
- SSL-MAC transforms for SHA-1, MD5
- AES-CCM, AES-XCBC-MAC, AES-CBC-MAC-PRF
- GHASH, GCM, AES-GCM and AES-GMAC
- CRC32
- Kasumi in f9 mode (UIA1)
- SNOW3G in basic and 128-EIA1 mode (UIA2)
- ZUC in basic and 128-EIA3 mode (UIA3)
The DMA controller supports:
- Scatter/Gather capability
- Source Address and Destination address of 32 bit
- Up to 2048 bytes per DMA transfer
- Automatic arbitration and bus flow control
- Big and little endian host systems
Master and slave interface:
- Master/Slave interface: AXI/AXI or AXI/APB or AHB/AHB slave interface
- Input and output buffers decouple Packet Engine from system bus interface
- Convenient SW debug interface including halt mode
- Clock switching interface for low power consumption
Resources
Videos