Home > Security IP > Provisioning and Key Management > CryptoManager Trusted Provisioning Services
Security
CryptoManager Trusted Provisioning Services
How CryptoManger Trusted Provisioning Services Works
A key component to the CryptoManager Platform, our trusted provisioning services enable improved security for SoCs, devices and secure applications by providing a trusted path for sensitive data throughout their lifecycle. This sensitive data can include cryptographic keys and configuration settings to enable application security; personalization information for applications, devices and users; and application, device, and service features; as well as other forms of sensitive information enabling device life-cycle management and robust on-device security services.
The CryptoManager secure in-field provisioning capabilities are based on trust established early in the manufacturing process through integration with the CryptoManager Security Engine as a robust on-device root-of-trust.
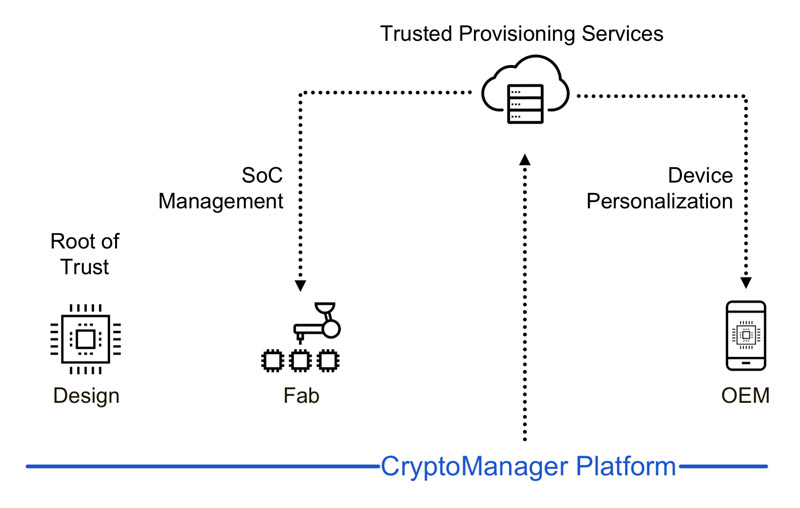
This enables a complete cloud-to-silicon full-lifecycle security ecosystem that provides a new level of protection for devices in the field, and fundamentally changes the way that trust is established and managed for mobile devices and applications.
A number of high value mobile application segments are dependent on strong device-side security to manage risks and enable mobile application services businesses. These applications include mobile payments, smart ticketing, content protection, and other applications requiring strong identity, security and trust. With the prospect of multiple trusted applications which, in turn, require support from a mix of trusted stakeholders within the mobile ecosystem, the need for a unified, secure, and trusted provisioning platform has become essential.

The CryptoManager Root of Trust
Built around a custom RISC-V CPU, the Rambus CryptoManager Root of Trust (CMRT) is at the forefront of a new category of programmable hardware-based security cores. Siloed from the primary processor, it is designed to securely run sensitive code, processes and algorithms. More specifically, the CMRT provides the primary processor with a full suite of security services, such as secure boot and runtime integrity, remote attestation and broad crypto acceleration for symmetric and asymmetric algorithms.Solution Offerings
- Via a hardware core, endpoint security that begins at the SoC manufacturing stage of the lifecycle through keys provisioned very early in the manufacturing process to a trust root integrated in the mobile device chipsets; or
- Via a software agent that runs in the trusted operating system or the high-level OS when the hardware core is not present, endpoint security for in-service devices and other devices that lack a hardware core.
- Full-lifecycle Cloud-to-Silicon Secure Provisioning
- Enables trusted manufacturing provisioning services to chipmakers and device makers at all levels of the supply chain
- Provides trusted in-field provisioning services for Apps whether pre-installed by the device maker or provided by a service provider and downloaded from the App Store
- Customer owned and operated infrastructure – for service providers and network operators who want the control and flexibility of deploying the infrastructure that enables secure provisioning services for in-field devices within their data centres
- Secure provisioning infrastructure provided as a cloud service – hosted infrastructure option for service providers focus on rapid time-to-market and low upfront investment.
- Supply chain process monitoring to ensure production volumes and process yields are being accurately measured
- In-field provisioning transaction reporting accurately tracks the delivery of sensitive keys and data, and enables simple and dependable services billing
- Breaks reliance on traditional centralized trust authorities to broker trust for in-service devices
- Service providers and operators can establish independent trust with devices, users, and applications to enable secure device services throughout the device lifecycle
- Comprehensive cloud service for customers who prefer to consume the CM Infrastructure for secure provisioning as a service rather than a product.
- Hosts, operates, and maintains all components of the CryptoManager Infrastructure, allowing application developers and service providers, to leverage the trust and security of CryptoManager without having to own and operate provisioning infrastructure.
- Includes tools allowing easy integration of access to the cloud service into existing customer backend platforms for key provisioning and feature management of applications.
- 24×7 Support and Maintenance of CM Device and System Software
- Integration, Test, and Deployment Guides as well as Setup Support professional services
- Customer Admin / Operator Training and Certifications
Use Cases
Personalization
Large OEM customers requesting personalization, customer specific data preparation and feature customization of standard parts challenge the chipmakers ability to minimize inventory overhead and improve operating efficiencies.
Secure Key Provisioning
With mobile devices housing more and more sensitive data that is utilized in a wide variety of applications, chip and device companies must meet the complex security requirements for each potential use case or capability.Debug Access Control
The CryptoManager solution provides a method for chip and device companies to authenticate the device and authorize the provisioning of the debug enable/disable operation for each device.
Resources
Videos