CryptoManager Device Key Management
Home > Security IP > Provisioning and Key Management > CryptoManager Device Key Management
CryptoManager Device Key Management is a cloud-based software platform enabling customers to build and deploy key management services that leverage hardware-provisioned keys and certificates in chips and devices over the entire device lifecycle.
How CryptoManager Device Key Management works
CryptoManager Device Key Management provides a cloud-based software platform which enables the building of key management services for chips and devices. Semiconductor and system OEMs can leverage these services to securely provision identities, device keys, and certificates to enable full lifecycle security management. CryptoManager Device Key Management enables an automated and secure capability to connect to trusted provisioning in manufacturing, and to leverage those provisioned identities and keys via the cloud to deliver value-add security services. These services provide chip and device makers additional opportunities to monetize their products after sale and shipment to end users.
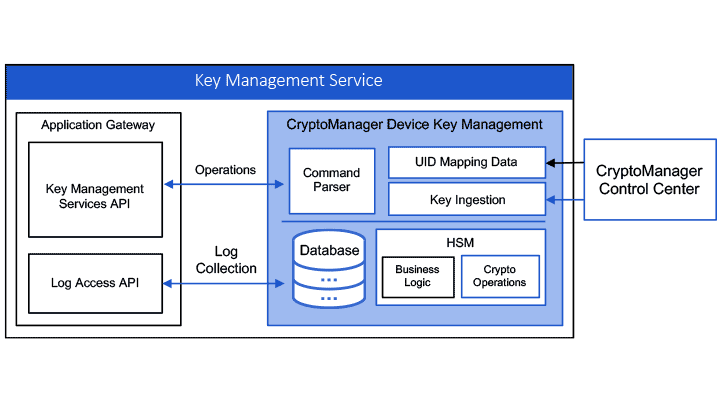
Key management services built on the CryptoManager Device Key Management platform consist of four major components:
- Cloud access proxy gateway that controls access to keys and related services
- Application gateway and associated APIs to deliver services
- Backend key and certificate database to store and manage keys and certifications
- Public key infrastructure (PKI) to provide certificate lifecycle management services
CryptoManager Device Key Management enables capabilities and services including:
- Verification of device ID and other chip/device meta data
- Retrieval or secure replacement of device keys
- Certificate issuance, delivery and revocation
The CryptoManager Device Key Management platform can be deployed in conjunction with CryptoManager Provisioning. CryptoManager Provisioning enables the injection of cryptographic keys and other sensitive data into semiconductors and devices throughout a distributed supply chain. CryptoManager Provisioning capabilities cover a broad range of secure operations, including key delivery and programming, protection of debug and other sensitive ports, and feature configuration for chips and devices.
Protecting Safety, Revenue and Brand: Combating Counterfeit Semiconductors in the Automotive Supply Chain
The counterfeit market for semiconductors is real, sizable and growing. Industry analysts peg the current market for fake semiconductors at $75B. Counterfeit chips pose great risk to driver comfort and safety, to say nothing of the severe negative consequences they present to automaker revenues and brand. The good news is there are immediate and cost-effective measures available to secure the semiconductor supply chain and stop counterfeiters in their tracks.Use Cases
Secure Supply Chain
Manufacturers can leverage securely provisioned keys and identities to enable supply chain integrity.
Trusted Identity
Device OEMs and end users can cryptographically
validate the identity of chips and devices at any
point in the device lifecycle.
Security as a Service
Chip and device OEMs can offer “security as a service” for post-sale monetization of key-based features and functions.
Resources
Videos