Home > Security IP > Trusted Services
Security
CryptoManager Trusted Services
Flexible cloud-to-silicon secure connectivity, analytics and security management product suite for service providers, operators, and OEMs.
| CryptoManager Components | Product Brief | Description |
|---|---|---|
| IoT Security Service | Turnkey Device to Cloud IoT Security Service for OEMs and Service Providers |

Security Lifecycle Management
Cloud-to-silicon Security Ecosystem across multiple chipset and PaaS architectures
Secure credential management, authentication, and device protection using encrypted communication

Seamless Secure Connectivity
Based on proven platform to provision billions of chips
Establish independent trust between devices and services throughout the device lifecycle

Flexible Platform Integration
Designed to integrate with multiple chipsets and PaaS architectures
Secure services implemented via a hardware or software root of trust
As the amount of valuable data stored and communicated across devices continues to grow in the mobile, automotive and IoT segments, the need for robust security services is becoming increasingly necessary. This issue is further compounded by the fractured ecosystem for devices and services across these segments.
The Rambus CryptoManager Trusted Services support a variety of root of trust configurations via a hardware core or secure software, providing a scalable and flexible security solution. Our solutions support out-of-the-box secure connectivity, credential provisioning and device security lifecycle management.
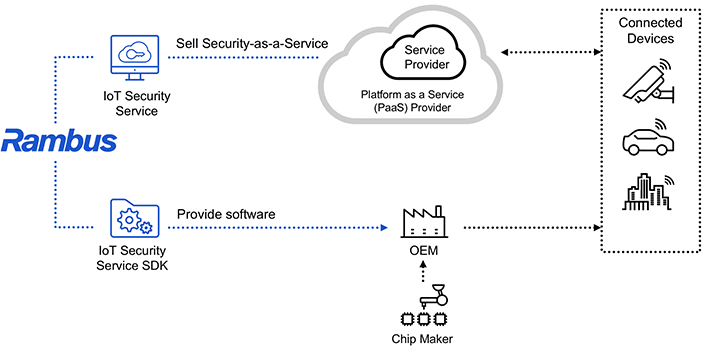
The CryptoManager IoT Security Service provides a turnkey Security-as-a-Service solution that protects service high-availability for OEMs and Service providers. Designed to support multiple chipset and PaaS architectures, our IoT Security Service.
Resources
Videos