Rambus has joined Microsemi Corporation’s System-on-Chip (SoC) Partner Program. This means Microsemi field programmable gate array (FPGA) customers can now select advanced security solutions developed by Rambus to protect against side-channel attacks for highly-sensitive markets, including aerospace and avionics.
The Partner Program agreement includes all differential power analysis (DPA) solutions developed by Rambus – including its DPA Resistant cryptographic cores and DPA Resistant software libraries. As part of Microsemi’s SoC Partner Program, Rambus will join other independent providers in providing FPGA design services and embedded software/hardware products supporting Microsemi devices. The program provides engineers with access to additional design resources, expertise and products from Microsemi’s network to enable faster time to market.
According to Eric Spanneut, vice president of the Rambus Security Division, Microsemi and Rambus have collaborated on security technology for several years. In addition, Microsemi was an early licensee of Rambus’ security offerings.
“Customers now have an option to add our proven security solutions into Microsemi FPGAs to mitigate the threat of DPA—a significant vulnerability in chip security facing multiple end markets, including mission-critical applications found in government and military settings,” he explained. “We are excited to team with Microsemi to deliver the right products, tools and services to keep customer products secure.”
Bruce Weyer, vice president and business unit manager at Microsemi, expressed similar sentiments.
“With the threat of side-channel attacks and other cybersecurity threats on the rise, our relationship with Rambus allows customers to inherently protect their valuable design intellectual property (IP), sensitive data and embedded systems, and ensures the rigorous security requirements of our defense, communications and industrial customers are being met,” he stated. “We look forward to an ongoing collaboration with Rambus so we can jointly deliver proven security solutions to our customers.”
As we’ve previously discussed on Rambus Press, Differential Power Analysis is a form of side-channel attack that monitors variations in the electrical power consumption or electro-magnetic emissions of a target device. The basic method involves partitioning a set of traces into subsets, then subsequently computing the difference of the averages of these subsets. Given enough traces, extremely minute correlations can be isolated—no matter how much noise is present in the measurements.
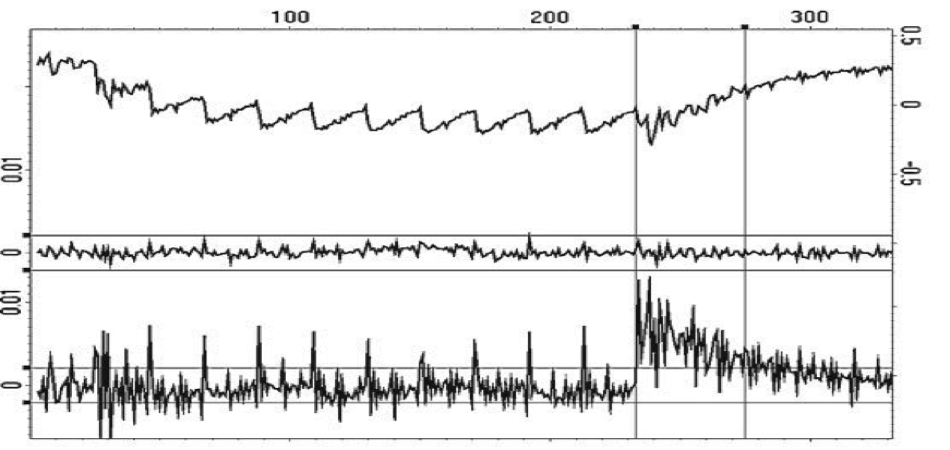
Image Credit: Rambus Security Division (via “Introduction to Differential Power Analysis”)
A typical DPA attack comprises 6 primary stages: communicating with a target device; recording power traces while the target device performs cryptographic operations; signal processing to remove errors and reduce noise; prediction and selection function generation to prepare and define for analysis; as well as computing the averages of input trace subsets and evaluating DPA test results to determine the most probable key guesses. Additional DPA variants include reverse engineering unknown S-boxes and algorithms, correlation power analysis (CPA), probability distribution analysis, high-order DPA and template attacks.
Specific DPA countermeasure techniques include decreasing the signal-to-noise ratio of the power side channel by reducing leakage (signal) or increasing noise, for example, by making the amount of power consumed less contingent upon data values and/or operation (balancing); introducing amplitude and temporal noise; incorporating randomness with blinding and masking by randomly altering the representation of secret parameters and implementing protocol-level countermeasures by continually refreshing and updating cryptographic protocols used by a device.
It should be noted that Rambus has licensed a range of DPA countermeasures to a number of prominent corporations such as Boeing, NVIDIA, Idaho Scientific, The Athena Group, Thales E-Security, NAGRA and Winbond.
Interested in learning more? You can check out our DPA countermeasures product page here.
