Defining smart cities
The U.S. Department of Homeland Security (DHS) defines smart cities as urban centers that integrate cyber-physical technologies and infrastructure to create environmental and economic efficiency while improving the overall quality of life. To accomplish this, smart cities gather and analyze data from IoT devices and sensors embedded in roadways, power grids, buildings and other infrastructure.
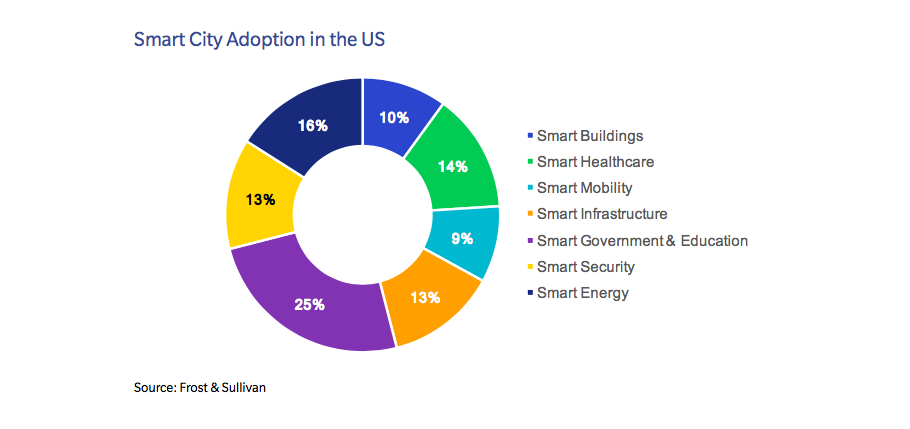
Smart city attack vectors
The interconnectedness of devices between cyber systems and the physical world creates a wide attack surface for malicious actors. Attackers could potentially target IoT devices comprising smart city infrastructure for a number of reasons, such as boasting rights, political grievances, financial gain (ransomware) and even terror. Prime targets include smart grids and meters, community energy management systems (CEMS), building energy management systems (BEMS), smart transportation, traffic lights, air quality monitoring systems, cellular networks, public Wi- Fi connections, data repositories and water-related infrastructure.
Targeted infrastructure
Perhaps not surprisingly, cyber criminals have already begun targeting smart city infrastructure around the globe. In 2016, San Francisco’s (MUNI) public transportation ticket machines were locked down after ransomware attackers demanded $73,000 – with passengers riding free until the issue was resolved.

Additional attacks include a hacked siren system in Dallas which jarred residents awake and flooded 911 with thousands of calls; a compromised electric transmission station which blacked out a portion of the Ukrainian capital (Kiev) equivalent to a fifth of its total power capacity; a DDoS offensive that halted heating distribution in at least two properties in the Finnish city of Lappeenranta during winter; and a digitally hijacked tram system in Poland that derailed four vehicles and injured 12 people.
Clearly, smart city devices, as well as the data they generate, must be protected against a wide range of cyber threats. Indeed, vulnerable devices can be hijacked and even physically disabled, while unencrypted or unverified data transmissions can be intercepted, leaked or spoofed.
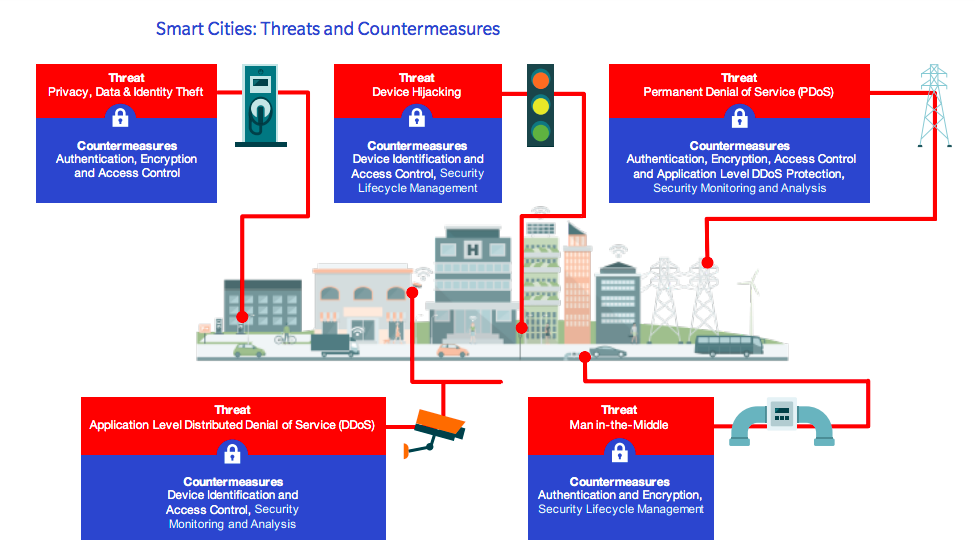
Despite the real-world risks, service providers and OEMs are understandably concerned that implementation of a comprehensive IoT security solution for smart city infrastructure could potentially incur additional costs and delay time to market. As such, the most effective security solution is one that does not negatively impact profitability or time to market. Put simply, a practical, simple and secure solution that can be easily and widely adopted by service providers is far more effective than a ‘super solution’ with only limited adoption.
Rambus CryptoManager IoT Device Management
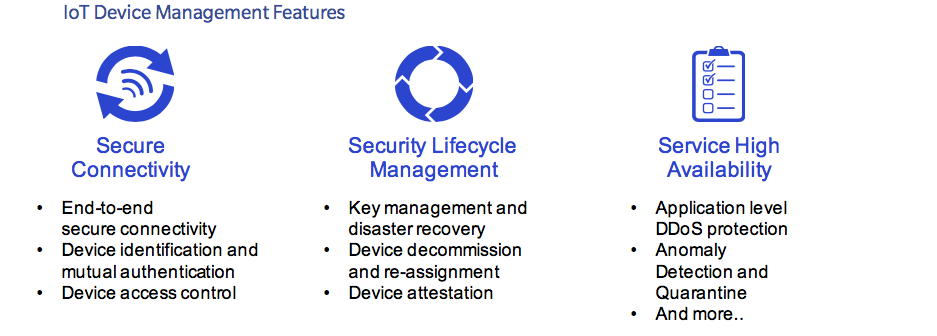
The Rambus CryptoManager IoT Device Management is a turnkey device-to-cloud solution that uses pre-provisioned unique device keys to automatically identify and authenticate a device. The device is then securely provisioned by IoT Device Management over the air, creating a secure communication channel between the device and the service. Features included in our one-stop-shop solution include seamless device-to-cloud secure connectivity, device lifecycle management, and advanced device monitoring capabilities to protect service high-availability and help mitigate a variety of attacks including distributed denial of service (DDoS).
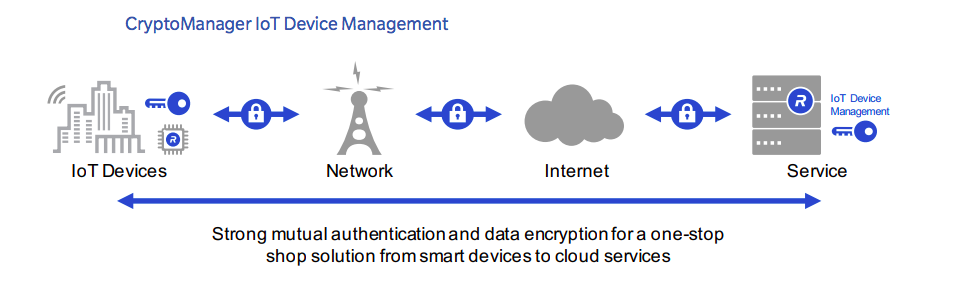
The CryptoManager IoT Device Management solution comprises multiple software modules that can be pre-integrated in smart city devices and the selected cloud Platform as a Service (PaaS). When a smart city device is powered up and connected to the internet, it automatically connects to the IoT Device Management service, seamlessly authenticates and provisions relevant security credentials.
Interested in learning more securing smart cities? You can download our white paper below.

