Michael Mehlberg, a senior director of business development at Rambus’ security division, recently wrote an article for Intelligent Aerospace about the importance of protecting military equipment – including avionics and electronics – from tampering, reverse engineering and cryptanalysis.
Have you read our primer?
– Side-channel attacks explained
“While cyber-warfare has become increasingly sophisticated in recent years, side-channel attacks conducted against sensitive electronic gear are relatively simple to execute and can be performed with less than $5,000 of standard lab equipment,” he explained.
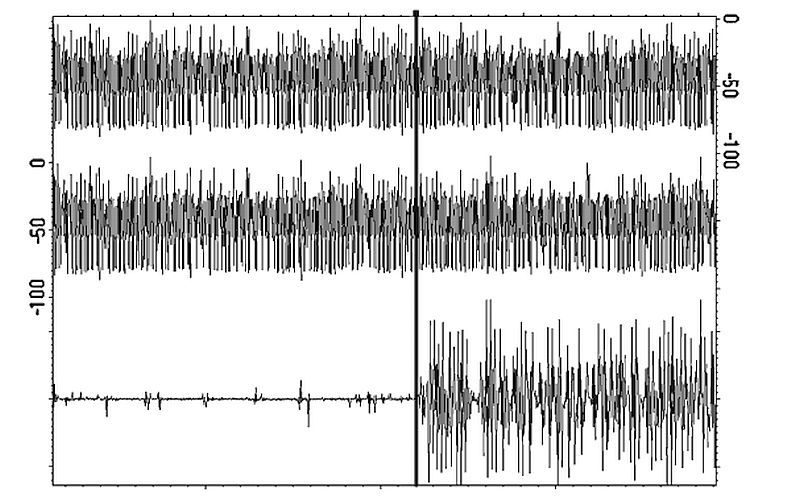
SPA illustration. Image Credit: Rambus Security Division (via “Introduction to Differential Power Analysis”)
“Such attacks include Simple Power Analysis (SPA) and Differential Power Analysis (DPA). These noninvasive techniques analyze power consumption while a device is performing routine operations with secret keys and algorithms.”
While no single countermeasure can effectively secure a system against all threats, Mehlberg says a layered approach that includes resistance against SPA and DPA attacks should be integrated into critical electronic systems.
“Military equipment and platforms may have evolved significantly since Soviet scientists reverse-engineered the Sidewinder missile in 1958 and North Korean soldiers boarded the Pueblo in 1968,” he continued. “Nevertheless, the threat of total mission compromise remains a clear and present danger, especially in close proximity to hostile territory. Indeed, equipment deployed at forward operating bases (FOBs) is particularly vulnerable.”

USS Pueblo. Image Credit: U.S. Navy Naval History and Heritage Command (via Wikipedia)
To be sure, although FOBs are routinely supported by Main Operating Bases, adverse conditions may act to temporarily delay resupply and reinforcements. Smaller Cooperative Security Locations (CSLs) – aka “lily pads” – face similar logistical difficulties as well. In addition, CSL personnel may be instructed to follow strict security protocols that effectively limit both incoming and outgoing communications. Therefore, says Mehlberg, it is critical for warfighters to be equipped with secure electronic equipment before they are deployed to FOBs and CSLs.
“As is the case with many deployed electronic systems, developers and systems integrators must take care to protect important equipment against unauthorized access in the event of a battlefield loss,” he elaborated. “Electronic communications equipment is of particular interest to those who may wish to intercept battlefield transmissions and should be specifically secured against unauthorized access of any kind.”

Forward Operating Base Logar, Afghanistan. Image Credit: U.S. Army (via Wikipedia)
More specifically, portable electronics, communications gear and “leave-behind” equipment are the most vulnerable to exploitation and could potentially allow hostile forces to eavesdrop on military communications and forge command-and-control messages. Therefore, equipment that employs cryptography to protect the sensitive transmission of data should be capable of resisting various forms of side-channel attacks, including DPA and SPA.
“These powerful, non-invasive attacks can be exploited by hostile elements to allow the unauthorized extraction of secret cryptographic keys, potentially revealing classified data. In fact, most tamper-resistant devices and cryptographic algorithms are susceptible to such attacks if they do not include countermeasures. Perhaps not surprisingly, general-purpose silicon – such as FPGAs and ASICs – receive more attacker attention because they are easier to acquire,” he added.
Interested in learning more about protecting military equipment from side-channel attacks? The full text of “Protecting military electronics, avionics from side-channel attacks,” is available on Intelligent Aerospace here. You can also check out our DPA countermeasures product page here.
