Semiconductor Engineering’s Ann Steffora Mutschler has written an in-depth article that explores the issue of transient power at 10/7nm. According to Mutschler, transient power adds yet another level of complexity for design teams already wrestling with power issues caused by leakage, a variety of power management techniques to control dynamic power and leakage current.
“At each new node there is less headroom for engineering teams to address these problems, and more likelihood that what they do in one area will affect another,” she explained.

“Threshold voltages already are pushing the limit, design margins are shrinking, and a push toward greater heterogeneity means more devices with their own power requirements are being crammed into these designs. Transient power is one more factor to deal with, and it adds to the collective problems of power and signal integrity.”
Mutschler also noted that concerns about security further complicate matters at 10/7nm, with side-channel attacks presenting a danger to chip designers. Preventing this type of breach, says Mutschler, requires an understanding of transient power – skill sets that normally don’t go together.
“Designers need to analyze the transient power waveform for a variety of usage scenarios to make sure that their chip will not be susceptible to side-channel attacks,” Andy Ladd, president and CEO of Baum, told Semiconductor Engineering. “In all of these cases, fast and accurate transient power analysis is key to optimizing and validating the design.”
As we’ve previously discussed on Rambus Press, side-channel attacks monitor power consumption and electro-magnetic emissions while a device is performing cryptographic operations. Side-channel attacks conducted against electronic devices and systems are relatively simple and inexpensive to execute. This means attackers can exploit various side-channel techniques to gather data and extract secret cryptographic keys.
In addition to implementing side-channel countermeasures, it is recommended that system and device designers evaluate resistance to side-channel attacks – including SPA, DPA, HO-DPA and EMA – before a product is brought to market. Platforms such as the DPA Workstation (DPAWS) measure a variety of side-channel attacks across a wide number of devices and platforms including smart phones, tablets, POS terminals, CPUs, TVs, set-top boxes, FPGAs, smart cards and NFC tech.
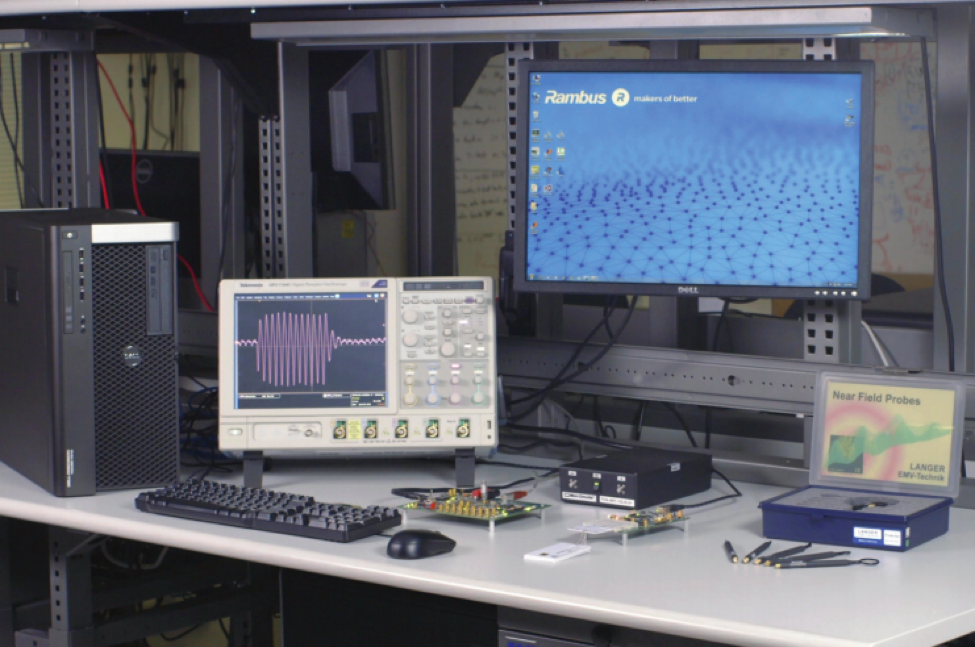
DPAWS provides users with a highly-intuitive UI paired with enhanced data visualization that creates an integrated, project-centric analytic environment specifically designed to optimize the efficiency of side-channel analysis. Both flexible and scalable, DPAWS easily integrates with a wide range of industry tools such as Matlab, as well as Python and other scripting languages. The DPA Workstation also supports full cipher coverage (AES, RSA, ECC, DES and SHA), large dataset handling, as well as high-speed collection and analysis of billions of traces.
Interested in learning more about side-channel attacks? You can check out our eBook on the subject below.

