PKA-IP-28 RSA/ECC Public Key Accelerators
Home > Security IP > Crypto Accelerator Cores > PKA-IP-28
The PKA-IP-28 is a family of Public Key Accelerator IP cores designed for full scalability and an optimal “performance over gate count” deployment. Proven in silicon, the PKA-IP-28 public key accelerator addresses the unique needs of semiconductor OEMs and provides a reliable and cost-effective solution that is easy to integrate into SoC designs. The PKA-IP-28 can be deployed in any semiconductor design that requires high performance/low power consumption key exchange or key generation.
NIST CAVP compliant for FIPS 140-3
How the PKA-IP-28 works
The PKA-IP-28 accelerates the following basic operations in hardware:
- Large vector addition, subtraction and combined addition/subtraction
- Large vector bit shift right or left
- Large vector multiplication, modulo and division (the latter generates both remainder and quotient)
- Large vector compare and copy
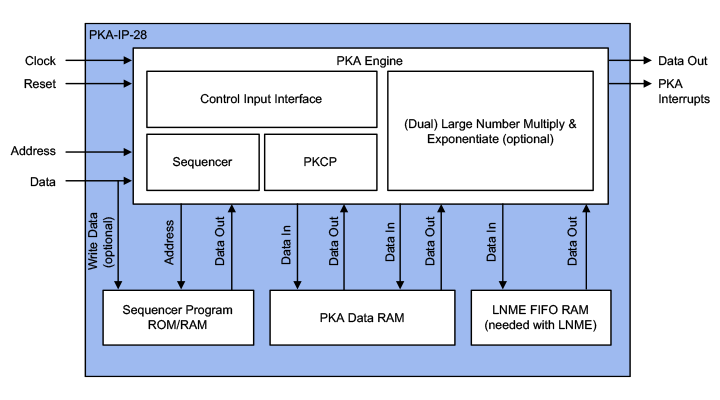
The PKA-IP-28 also accelerates the following complex operations, under control of an embedded sequencer microcontroller, using locally stored firmware:
- Large vector unsigned value modular exponentiation
- Large vector unsigned value modular exponentiation using the ‘Chinese Remainders Theorem’ (‘CRT’) method with pre-calculated Q inverse vector
- Modular inversion: given A and M, calculate B such that ((AB) MOD M) = 1
- Prime field ECC point addition/doubling on elliptic curve y2=x3+ax+b (mod p) with ‘p’ a prime number and ‘a’ and ‘b’ input values to the operation, adding identical points automatically performs point doubling – operation can be performed with affine and projective points
- Prime field ECC point multiplication on elliptic curve y2=x3+ax+b (mod p) with ‘p’ a prime number and ‘a’ and ‘b’ input values to the operation – a version of the ‘Montgomery ladder’ algorithm, point randomization and point-on-curve checking are used to provide side channel attack protection The Sequencer firmware hides the fact that the modular exponentiations and ECC point multiplication are done using numbers in the Montgomery domain. For improved performance of modular exponentiation operations, the Public Key Accelerator employs exponent recoding techniques that use a table with pre-calculated odd powers (filling this table is performed by the sequencer firmware). The smallest configurations can optionally use the ‘Montgomery Ladder’ algorithm for modular exponentiation (lower performance but fixed timing).
PKA-IP-28 Applications
PKA-IP-28 public key accelerators are suitable for a wide range of applications:
- IoT, mobile, or other small gate count applications for secure boot, software public key signature checking and ‘occasional’ public key operations as used for IPsec and MACsec channel setup and firmware download signatures
- Secure router boxes, secure network interfaces and SSL servers, where the PKA-IP-28 is used in medium to high performance (Elliptic Curve) Diffie-Hellman key negotiation engines
- Hardware security modules, used in medium to high performance secure public key signature generator/checker engines
The PKA-IP-28 is available in nine different performance configurations ranging from 19K to 515K gates, each providing the full set of PKA operations with up to 4160-bit modulus size for modular exponentiations and 768-bit modulus for prime field ECC operations. The PKA-IP-28 is a security conscious design and can be provided with or without protection against side channel attacks. The PKA-IP-28 is also available as embedded PKA in our VaultIP and PKA-IP-154 product lines.
PKA-IP-28 Performance and Interfaces
Frequency
- 45nm: 400MHz
- 28nm: 700Mhz
- 16nm: 800MHz
In 28nm, performance of 700MHz is possible. In 16nm, 800MHz is possible. Performance scales with smaller process nodes.
Host Interfaces:
- TCM target interface for configuration and control
- Also available as PKA-IP-150 with AMBA slave (AXI or AHB).
- Local memories:
- 2K or 4K Byte data RAM (1K and 8K Byte possible)
- 2K … 4K words of 32-bits program RAM (ROM optional)
- 47 … 132 words of 32-bits FIFO RAM for faster configurations
- Interrupt outputs (functional and alarm)

Introduction to Side-Channel Attacks
Side-channel attacks conducted against electronic gear are relatively simple and inexpensive to execute. Such attacks include simple power analysis (SPA) and Differential Power Analysis (DPA). As all physical electronic systems routinely leak information, effective side-channel countermeasures should be implemented at the design stage to ensure protection of sensitive keys and data.



