Paul Kocher, President and Chief Scientist of Cryptography Research, discusses the importance of defending against differential power analysis attacks.

Paul Kocher, President and Chief Scientist of Cryptography Research, discusses the importance of defending against differential power analysis attacks.

Paul Kocher, President and Chief Scientist of Cryptography Research, discusses the importance of defending against differential power analysis attacks.

Architecture is constantly evolving – changing style, form and application. But through all of its evolutions from physical to digital, architecture matters. The physical and digital world blur as sensors translate activity into data. Ubiquitous sensors load today’s internet with boundless volumes of data. This requires a sophisticated architecture to optimize performance with minimal power. An architecture that supports the massive amount of data being captured. Secured. Moved.
The continued proliferation of power-efficient mobile technologies, cloud computing, and pervasive connectivity has fostered an increasingly connected world and given rise to The Internet of Things. This is how Rambus sees the future.

Connected products, including mobile phones and Internet of Things (IoT) devices have a critical need for security. Robust security starts with the design of the SoC and continues with the manufacturing supply chain. The CryptoManager solution brings revolutionary security improvements to the semiconductor chips and supply chains that enable our mobile world.
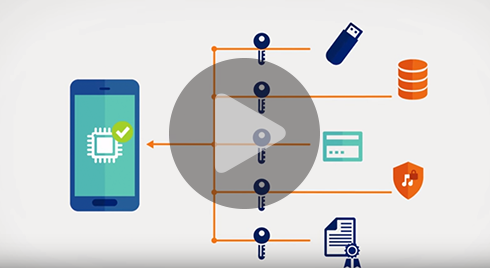
Differential power analysis is a powerful tool attackers used to extract secret keys and compromise the security of tamper resistant devices. DPA is a side-channel attack that is extremely effective low cost and widely known. These attacks use variations in the electrical power consumption of a targeted device and then breech security in devices by using statistical methods by deriving secret keys from crypto-algorithm. DPA attacks are dangerous because they circumvent the normal hardware and software security defenses that have been put in place, allowing fraudulent transactions, data theft, device modifications and other costly, unauthorized activities. Because such attacks are noninvasive, an intruder can compromise an embedded system without leaving a trace.
To learn how Rambus Security is guarding DPA attacks, click here.

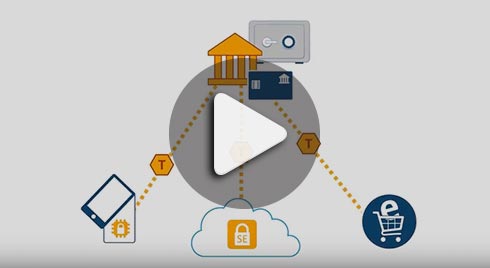
Traditionally when a card or mobile payment is made, the card number passes through various points in the authorization process. This increases the risk of fraud because this data can be intercepted at multiple points. To counter this, an increasing amount of payment card issuers use a technology called tokenization. This stores the original number in a secure token vault, and substitutes it with a unique tokenized number. Because of the limited validity, this number is useless when intercepted.
To learn more about tokenization and how Rambus is securing mobile payments, click here.