Rambus has signed a patent license agreement with Beijing Tongfang Microelectronics Co., Ltd, a fabless chip design company that focuses on smart cards and related technologies.

The agreement includes the use of Rambus patents such as Differential Power Analysis (DPA) Countermeasures, which protect devices and integrated circuits against DPA and other related side-channel attacks (SCA). Much like safecracking, electronic side-channel attacks eschew a brute force approach to extracting keys and other secret information from a device or system. SCA conducted against electronic devices and systems are non-intrusive, relatively simple and inexpensive to execute.
“We are excited to deliver critical technology for protecting sensitive keys and data to Beijing Tongfang Microelectronics Co., Ltd.,” said Bret Sewell, senior vice president and general manager of the Rambus Security Division.
Differential Power Analysis
Differential Power Analysis (DPA) is a form of side-channel attack that monitors variations in the electrical power consumption or electro-magnetic emissions of a target device. The basic method involves partitioning a set of traces into subsets, then subsequently computing the difference of the averages of these subsets. A trace refers to a set of power consumption measurements taken while the device is performing cryptographic operations. Given enough traces, extremely minute correlations can be isolated — no matter how much noise is present in the measurements.
An example of the traces collected during a cryptographic operation is shown below in Figure 1.
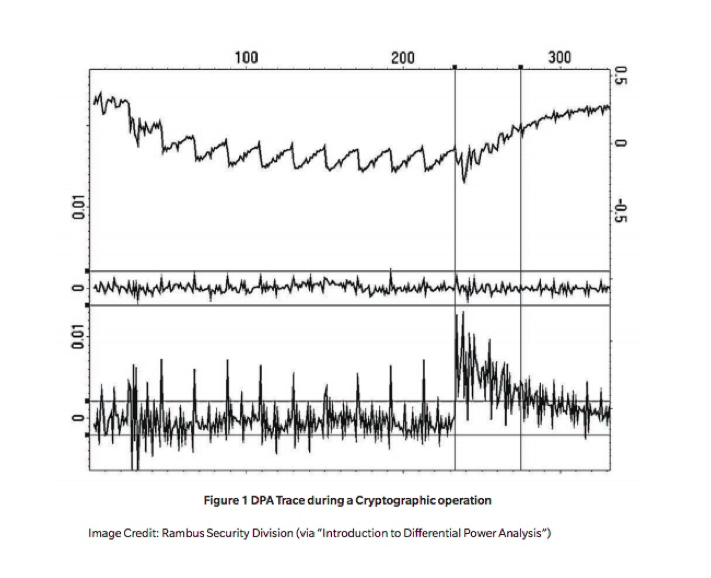
The top trace shows the DPA results showing the average power trace for an AES-128 operation running on an FPGA. The DPA process was used to find the bytes of the last round key used in the AES operation. The middle trace is a differential trace for a DPA test carried out with an incorrect guess of the first byte of the last round key and the bottom trace shows the corresponding differential trace for the correct key byte guess.
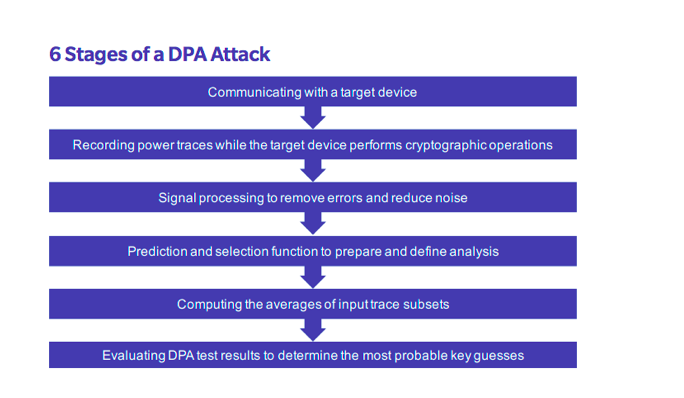
A typical DPA attack comprises 6 primary stages: communicating with a target device; recording power traces while the target device performs cryptographic operations; signal processing to remove errors and reduce noise; prediction and selection function generation to prepare and define for analysis; as well as computing the averages of input trace subsets and evaluating DPA test results to determine the most probable key guesses.
Additional DPA variants include reverse engineering unknown S-boxes and algorithms, correlation power analysis (CPA), probability distribution analysis, high-order DPA and template attacks.
DPA countermeasures
Specific DPA countermeasure techniques include decreasing the signal-to-noise ratio of the power side channel by reducing leakage (signal) or increasing noise, for example, by making the amount of power consumed less contingent upon data values and/or operation (balancing); introducing amplitude and temporal noise; incorporating randomness with blinding and masking by randomly altering the representation of secret parameters and implementing protocol-level countermeasures by continually refreshing and updating cryptographic protocols used by a device.

Because all physical electronic systems routinely leak information, an effective layer of side-channel countermeasures should be implemented via hardware (DPA resistant cores), software (DPA resistant libraries) or both. It should be noted that stand-alone noise introduction is incapable of sufficiently masking side-channel emissions. Indeed, DPA conducted against a device can effectively bypass stand-alone noise countermeasures, ultimately allowing the signal to be isolated. After layered countermeasures have been implemented, systems should be carefully evaluated with a Test Vector Leakage Assessment (TVLA) platform such as the Rambus DPA Workstation (DPAWS) to confirm the cessation of sensitive side-channel leakage.
Interested in learning more about Rambus’ DPA countermeasures? You can check out our product page here and download our eBook on the subject below.

